Tip of the Week: Your Desktop Needs Some TLC, Too

Does your business struggle with maintaining its Windows workstations? If you do, we fully understand any frustrations you might have. It can be challenging and time-consuming to keep your technology in proper working order, but it doesn’t have to be. With a couple of proactive tips to help you better manage your computers, you’ll be able to waste less time and stay productive during your workday.
Tip of the Week: Know Exactly How Far It Is from Point A To Point B With Google Maps

Who needs a GPS device when you have all that you need, right in your pocket? We’re talking, of course, about your smartphone. Whether you have an Android device or an iPhone, Google Maps can make for a great alternative, and it sure beats trying to use an atlas. You can use Google Maps to chart the distance between any target destinations and your current location. You can even use it to get the total distance for an upcoming vacation.
Before you get started, take a moment to make sure that you have the latest version of your Google Maps app for multiple platforms, including iOS or Android. You can find it on the Play store or iTunes.
You can start by opening the Google Maps app and navigating to the place you want to measure distance to. All you do is drop a pin on the location by tapping it. You can then proceed to expand the menu at the bottom of the screen and tap Measure distance. The location will appear in a set of crosshairs on the map.
The next step is to add another point near your location. You can just use whatever bend in the road is closest to your current location. The app will then calculate the distance between your points after you place each one. Once you’ve accomplished this, just select Measure Distance.
One notable thing to keep in mind is that the app can only tell you the distance between your desired location and your current location if you took a direct route there. It’s likely that there will be lots of complications if you drove your car there in a straight line. To tell the driving distance from one location to the next, you must place points all along the streets you’ll use to get to your location. This lets you calculate the exact distance you’ll be travelling.
If you like these tips and tricks, share these blogs on your social media accounts!
Tip of the Week: 5 Reminders To Protect You Against Ransomware

The Internet is a vast place filled to the brim with threats, especially for businesses that need to preserve the integrity of their infrastructure and keep critical data safe. The Cisco 2017 Annual Cybersecurity Report states that ransomware is growing at a yearly rate of 350%, which is a considerable number to say the least. Here are five tips that can help you keep your business safe from ransomware infections.
Remember Your Employees
Often times it’s your employees who are the first to come into contact with ransomware. Ransomware is often spread through spam messages that lurk in the inboxes of your employees. It’s best to educate them on how to avoid ransomware in the first place, as it can quickly become a pain to deal with once ransomware makes its home on your network.
Don’t Pay the Ransom
Even if your data is threatened by ransomware, it’s not worth paying the ransom to get it back. The mindset you need to keep is that you have to assume the worst. What if you pay up and you don’t get your data back at all? You can’t trust crooks to keep their word. You’re better off reaching out to a trusted IT service provider for assistance with your predicament.
Take Regular Backups
Since you can’t trust hackers to hand over the decryption key, you’ll have to resort to a more reliable way of ensuring your data’s safety. Data backup can help you prepare for the day you need to restore your data following a disaster. The ideal data backup solution will take multiple backups of your data several times throughout the day, and send them to an off-site data center or the cloud for safekeeping. The idea here is to make sure that your data backups aren’t stored on an infected network so that they will work properly when push comes to shove.
Ensure Your Security is Up to Date
Ransomware is always trying everything it can to slip through the cracks found in enterprise security. Therefore, you must take a proactive stance by updating your network’s security protocol so that all known variants of malware can be kept out of your infrastructure. This includes updating your software solutions, including your operating system and applications, to ensure maximum security.
Be Wary of Email
As we mentioned before, ransomware prefers email as its movement medium. Encourage any and all users on your network to be cautious of any unsolicited messages–especially those that contain links and attachments.
Microsoft users who want to find out more about ransomware can do so at the Ransomware FAQ that is regularly updated in the Windows Defender Security Intelligence (WDSI) database of threats. If you want a more personalized approach to ransomware security, however, reach out to Catalyst Technology Group at (317) 705-0333.
Tip of the Week: IT Has A Lot Of Jargon… How Much Do You Know?

If you spend more than ten minutes with anyone from the technology industry, you may notice that they have a rather colorful vocabulary. It’s not too vulgar or anything, but it is chock-full of buzzwords that you may not fully understand. Here are some of the most frequently used words in the IT industry.
Actionable Analytics
Businesses are capable of harnessing the power of analytics like never before. However, it’s important to remember that only certain data will actually be useful. The data that can be used to improve operations and measure progress is called actionable analytics, and it’s likely some of the most important data you’ll acquire.
Artificial Intelligence
Suspend any knowledge of artificial intelligence that science-fiction movies like The Matrix or Terminator have introduced over the years, and consider instead what intelligent technology can do for your business. You can use it to process lots of data all at once, or make educated decisions using this data. Other types of machinery are capable of speech recognition, learning, planning, and even problem solving.
Blockchain
Blockchain technology is pretty complicated, but the basic idea of it is that each time a file is changed, the changes are recorded, encrypted, and stored in a change log that cannot be edited or changed in any way. Blockchain technology is used in most cryptocurrency transactions, but also has uses in electronic medical records and legal agreements.
Chatbots
Chatbots are commonly considered programs that can build upon conversation, whether it’s through a chat window or spoken over the phone. It’s basically a way to automate certain functions for your business, allowing individuals or groups to get the support they need, even if they don’t speak a specific language. Chatbots can use databases and natural language processing to translate sentences in one language to another.
Cloud-Based Services
Cloud computing has allowed organizations to offer their assets “as a service.” What this means is that services can be delegated to organizations in a scalable, affordable, cloud-based environment that defies the boundaries of traditional hardware and software infrastructures. Furthermore, the company offering the services is generally responsible for any maintenance or security the service requires, while providing the consumer with the ability to control user permissions. Let’s say you purchase virtual server space–you pay a monthly fee, which keeps you from purchasing an entirely new server unit. It’s a considerable cost savings, to say the least.
Datafication
Since businesses are digitizing so much data, it is now being analyzed to transform the way that it’s utilized. This is called datafication, which is the process of turning aspects of everyday life into data that can be used for various purposes. One example is using social media to understand just who your potential employees are. In this sense, social media can, to an extent, replace personality tests. In fact, analyzing data is often a more accurate gauge of character than a personality test.
Decentralized Cryptocurrency
Cryptocurrency is something that is often used on the dark web to make sketchy sales. On the other side of the coin, however, is the ability to send and receive private, encrypted transactions outside of traditional banking. Cryptocurrency is a virtual asset that doesn’t rely on a physical currency to function, so in a lot of ways, it’s useful. One example of a rather popular cryptocurrency is BitCoin.
Gamification
When they first entered the computing world, video games made a huge splash. Chances are that your younger workers grew up with video games in at least some capacity. You can use this to your advantage with gamification techniques designed to enhance productivity through making work fun–or, at the very least, offering goals or “experience points” for your team to meet. If they earn enough points, they can level up and earn a reward.
Machine Learning
Machine learning is an aspect of artificial intelligence that allows a computer to collect data from different sources, and transform that data into reliable predictions. Businesses might use this information to make educated decisions about their future. For example, a company could use machine learning to collect data from potential customers and use it to increase the possibility that the target would buy specific products or services.
Microservices
If you don’t want each and every service that an application or a program has to offer, there’s often the choice to invest in a microservice, which breaks each of these features down into bite-sized pieces. You can then pay for them individually so as not to purchase services that you don’t need, and they can easily be swapped out or changed as needed.
Open Source
Open-source programs are built off of public source code that can be modified to suit the general needs of the organization. It’s often free and available for any organization that wants to use it. Businesses that want to create custom-made applications can often use open-source code to build working applications with a negligible price margin.
For more information about the many, and often confusing, words in the IT technician’s vocabulary, reach out to Catalyst Technology Group at (317) 705-0333.
Tip of the Week: Improving Outlook With Three Tips

Does your business use Microsoft Outlook as its preferred email client? It’s likely that you have already noticed how dynamic of a solution it is for your business purposes, but little do you know that the most recent version of Outlook is stacked with some of the best features out there to make your user experience even better.
Here are three of the best ways you can use Outlook to get more productivity out of your workday.
Quickly Access Your Inbox
If you want to access your inbox without going through all sorts of folders or icons, you can easily do so with just a few keystrokes. Just press the Windows key and R, and you’ll open the Run window. Just type outlook into the field.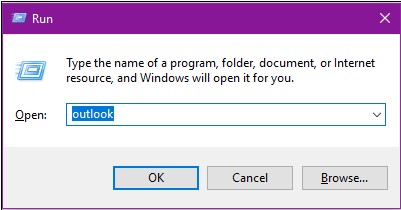
Add an Attachment
If you’ve worked in Excel or Word on a document, or recently downloaded a PDF or image file that you want to attach to an email, you can do that easily with Outlook. Outlook pulls any documents that you’ve recently opened and allows you to quickly attach it to a message.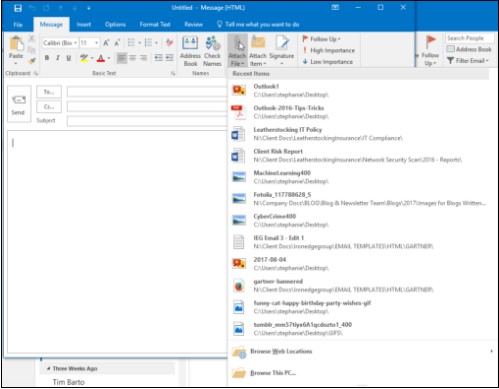
Deleting and Archiving
If you delete a file, it will be sent to your Delete folder. Delete folders are emptied from time to time, and once they have been emptied, the emails will be gone for good.
If you archive a file, it goes to the Archive folder. Archives messages will be removed from your inbox, but will keep them stashed away for later viewing. You can even set your emails to auto archive so that you don’t have to worry about doing it manually.
For more great tips and tricks about Microsoft Outlook and other Microsoft services, subscribe to the Catalyst Technology Group blog.
Tip of the Week: Little-Known Windows Features

Windows 10 is a valuable asset for any business, but are you taking full advantage of it? We’ll discuss some of the lesser known tips and tricks that your organization can take advantage of to get more out of your business technology.
Show Your Desktop
Have you ever been in a situation where you have many different applications open, all at the same time, and they cover your entire screen? This keeps you from seeing your desktop, which can be a major inconvenience. There is a very easy way to check your desktop, even if it’s covered with applications, and you certainly don’t have to close or minimize all of your programs. All you have to do is locate the little button on the bottom-right corner of the taskbar. It’s a bit slim, so we don’t blame you for not seeing it. All the way on the right, past the time and date and the notifications section, you’ll see a sliver of a button–this is what you want to click on.
Rotate Your Screen
To rotate your screen, you can use the keyboard shortcut. Ctrl+Alt+D, as well as the direction button, will allow you to rotate your screen 90 degrees in whichever direction you indicate with your keystroke. Even if this doesn’t have any real practical use, you might be able to use it to rotate an image or document that isn’t already in the right position.
Right-Click the Start Menu Tiles and Taskbar
You can right-click the Start menu to customize any tiles located in it. You can do various things with them, like adjust their size, unpin the tiles from the Start menu, or turn off the live tiles that are out of place. You can also do various things with your taskbar by right-clicking it, such as adding shortcuts, activating Cortana, and more.
If Windows 10 tips and tricks are what you crave, look no further. To learn more about your business technology, subscribe to Catalyst Technology Group’s blog.
Tip of the Week: Be Better At Microsoft Word With These Four Tricks

Microsoft Word is a great tool that your business may use for word processing, but it can do so much more. With the right tools, you’ll be able to take advantage of many different tricks that could change the way you see Microsoft Word. Here are four neat tips that you may not have thought of.
Create Quick Bullets
To add a bulleted list to your document, you can dodge the step of looking in the taskbar. To do so, just type in an asterisk (*) followed by a space. Place the text that you want bulleted next in this sequence. Word will automatically format this bulleted text for you. If you would rather have the text dashed, you could simply place a hyphen before the text, or do the same thing with numbers.
Randomly Generate Dummy Text
To ensure that your documents look the way you want them to, you can use simple dummy text as filler while you build a template. While the Internet is certainly a viable option for finding dummy text, you can generate it for yourself right in Microsoft Word. Just type in =rand(#) and replace the pound symbol with the number of paragraphs that you want. Once you’ve done this, press Enter and you should have all of the dummy text you could possibly want. This is particularly helpful when you want to test the formatting or fonts of your documents.
Quick Tables
If you need a table in your Word document, you could go through Excel to put one in it. If you don’t want to do this, you can just do it through Microsoft Word itself. Press “+” then “Tab”. Press another “+” and another “Tab”. Continue this until your table is the size that you want it to be and press “Enter” to form the table borders. If you’d like to increase the size of your table after pressing enter, you can simply click inside the very last box of the table and press tab until your table has reached the size you’d like it to be.
Select a Single Sentence
How accurate do you find the click-and-drag method for your mouse? If you want to try something different, you can use this shortcut to select a whole sentence in Microsoft Word. Simply press the Ctrl key and click a word in the sentence that you’re selecting. This lets you select the entire sentence, letting you delete it or move it as you like. You could even do something like click and drag it around before you release Ctrl to move it. If you want to make it a new paragraph, just click a word in that paragraph three times in a row.
There are almost countless Microsoft Word tips and tricks that you could be using to take better advantage of your business technology. Are you using them? To learn more about how you can use Microsoft Word and other software solutions for greater benefit, subscribe to Catalyst Technology Group’s blog.
Tip of the Week: Dynamic Lock Isn’t Perfect, But It’s A Start

You’ve been told that it’s a best practice to ensure that you never leave your workstation without locking it first. Yet, if you’re only stepping away for a few minutes, it might be tempting to just allow it to remain unlocked. But what happens when you step away for longer than expected? You leave your computer exposed to all manners of threats. Thankfully, a new solution allows for a fix with a device that most are never without: the smartphone.
This trick lies in your computer having the Windows 10 Creators Update installed, which lets you connect your phone to your PC through Bluetooth. This helps your PC automatically lock itself when the two are separated. Thanks to a piconet, a type of short-range radio wave network that keeps Bluetooth devices working properly, this security measure is possible. Of course, the strength of the piconet will determine how far from your PC the device can be before the computer locks.
This Creators Update can help you create a piconet between your desktop and phone, which keeps Dynamic Lock from activating. If you remove the phone from the piconet’s range, Dynamic Lock will lock your computer to keep unauthorized users from using it.
Just keep in mind that Dynamic Lock is far from instantaneous. The device needs to be out of range, and the computer needs time to register that the connection has been severed. Only then will Dynamic Lock activate. Keeping this in mind, it’s still more secure to implement Dynamic Lock than leaving your computer unlocked all the time.
How to Set Up Dynamic Lock
To pair your phone to your PC, you want to confirm with your IT department that it won’t be an issue. Just reach out to them before following this procedure.
First, enable Bluetooth on your mobile device that you want to pair with your PC. Open Settings and access Bluetooth & Other Devices. Next, click Add Bluetooth or Other Device, which will prompt the Add a device box.
Once you’ve done this, select Bluetooth. Windows may take a moment to find your device, but once it does, it will prompt you to confirm a code that displays on both of your devices. Once you’ve done so and click Done, you’ll be brought back to the Bluetooth & Other Devices page in your Settings, where you can see your connected device.
Select Home and navigate to Accounts, where you’ll want to select Sign-In Options. You’ll find Dynamic Lock, where you check the box called Allow Windows to Detect When You’re Away and Automatically Lock the Device. Restart your PC to make sure the settings have been changed, and you’ll be all set. The only thing left to do is try it out!
For more great tips and tricks, be sure to subscribe to Catalyst Technology Group’s blog.
Tip of the Week: Preserve Your Privacy With These 3 Websites

With the explosive popularity of social networking, the Internet seems to be a less private place than ever. With both communication and cyber crime rising in commonality, online privacy seems to be turning into a less attainable goal than ever. However, for this week’s tip, we’ll review some of the tools out there that can help you fight for your right to privacy.
Account Killer
How many email accounts have you accumulated in your life? How many do you still currently use? Chances are, the first number is much larger than the second, which means that you have plenty of potential vulnerabilities lying around for a hacker to find and exploit. Account Killer does exactly what it says on the box, allowing you to delete unused accounts and shore up potential vulnerabilities.
Have I Been Pwned
This website gives users an outlet to check if one of their online accounts has ever been involved in a cybercrime or breach event. By securely entering their email address, they can run a search of Have I Been Pwned’s database of nearly 4 billion compromised records to establish if any of their accounts may have been compromised, and which ones were. This one may be one to run periodically, as you never know when one of your accounts may have been involved in a breach.
DuckDuckGo
While it may have a questionable reputation, anonymous browsing has some uses for those doing a search online that they don’t want someone to see later. For example, anonymous browsing can enable you to search for a gift for someone else with access to the computer without fear of their discovering your activity. This variety of browsing can also land the lowest rates for airfare, as travel websites will often offer better deals when they are unsure where you are originally located.
At the end of the day, it is much simpler to avoid digital privacy issues than it is to fix them after the fact. After all, the Internet has a very long memory.
For more data security tips and best practices, keep checking in to our blog.


