Tip of the Week: Dynamic Lock Isn’t Perfect, But It’s A Start

You’ve been told that it’s a best practice to ensure that you never leave your workstation without locking it first. Yet, if you’re only stepping away for a few minutes, it might be tempting to just allow it to remain unlocked. But what happens when you step away for longer than expected? You leave your computer exposed to all manners of threats. Thankfully, a new solution allows for a fix with a device that most are never without: the smartphone.
This trick lies in your computer having the Windows 10 Creators Update installed, which lets you connect your phone to your PC through Bluetooth. This helps your PC automatically lock itself when the two are separated. Thanks to a piconet, a type of short-range radio wave network that keeps Bluetooth devices working properly, this security measure is possible. Of course, the strength of the piconet will determine how far from your PC the device can be before the computer locks.
This Creators Update can help you create a piconet between your desktop and phone, which keeps Dynamic Lock from activating. If you remove the phone from the piconet’s range, Dynamic Lock will lock your computer to keep unauthorized users from using it.
Just keep in mind that Dynamic Lock is far from instantaneous. The device needs to be out of range, and the computer needs time to register that the connection has been severed. Only then will Dynamic Lock activate. Keeping this in mind, it’s still more secure to implement Dynamic Lock than leaving your computer unlocked all the time.
How to Set Up Dynamic Lock
To pair your phone to your PC, you want to confirm with your IT department that it won’t be an issue. Just reach out to them before following this procedure.
First, enable Bluetooth on your mobile device that you want to pair with your PC. Open Settings and access Bluetooth & Other Devices. Next, click Add Bluetooth or Other Device, which will prompt the Add a device box.
Once you’ve done this, select Bluetooth. Windows may take a moment to find your device, but once it does, it will prompt you to confirm a code that displays on both of your devices. Once you’ve done so and click Done, you’ll be brought back to the Bluetooth & Other Devices page in your Settings, where you can see your connected device.
Select Home and navigate to Accounts, where you’ll want to select Sign-In Options. You’ll find Dynamic Lock, where you check the box called Allow Windows to Detect When You’re Away and Automatically Lock the Device. Restart your PC to make sure the settings have been changed, and you’ll be all set. The only thing left to do is try it out!
For more great tips and tricks, be sure to subscribe to Catalyst Technology Group’s blog.
Do You Need Data Backup? The Answer: Absolutely

Data backup is something of a conundrum for many small businesses. The classic mindset is that they don’t think they need data backup because there’s no way they’ll be struck with a data loss disaster. Their office may not be located in a place prone to natural disasters, and the organization is so small that the assume they are off the hook when it comes to hackers. This doesn’t reduce the value that a good data backup system can offer, though.
Having a “it won’t happen to me” mentality will only make it hurt even more in the event that your business does suffer data loss. Many problems can result in data loss; hardware failures, end-user errors, surges and lightning, fires, and floods, can all leave you stranded. Here are three indicators that you know you need a proper data backup system.
You Regularly Use Contact Information and Other Data
Data that’s crucial for operations is of the utmost importance for your business. If you happen to lose it due to a disaster or a user error, you’re out of luck if you don’t have some sort of data backup system implemented. If your line of work depends on this data, you need to do everything in your power to protect it from any circumstances that could lead to its destruction or loss.
You Need to Access Historical Files and/or Records
Depending on your industry and the regulations that come with it, you might be required to keep a backup of your data. There may be other requirements as well, such as keeping your data off site or encrypted.
Your Employees Need It
Nobody is perfect. Even your most seasoned sales person might accidentally save over the only copy of your sales proposal template. Being able to quickly pull a single file or folder from a backup will save a lot of time and frustration. It’s also important to have a backup for your business if you want to ensure your employees’ retention. 60 percent of businesses that suffer a major data loss event file for bankruptcy within 6 months.
You Frequently Experience IT Troubles
If your technology isn’t the most reliable equipment out there, you should consider implementing a full data backup and disaster recovery solution. Hardware failure is a common reason why organizations lose data, simply because it seems to come out of nowhere. There are warning signs, though, if you know where to look. If your hardware starts to make strange noises, experiences operational inefficiencies, and is generally more trouble than it’s worth, data backup is critical.
You Don’t Have One At All!
To not be using some type of backup system is, in a word, risky. Ultimately, having a data backup and disaster recovery solution is a great preventative measure to take advantage of in a perilous and unpredictable technology field. Even something as simple as an onsite backup solution is better than not having one at all. However, you’ll want only the best solution for your business’s needs, so we recommend taking full advantage of our cloud-based Backup and Disaster Recovery (BDR) solution.
Could your business use a hand with implementing data backup and disaster recovery? If so, reach out to Catalyst Technology Group at (317) 705-0333.
Need A Better Method Of Software Acquisition?

What are some of the critical business applications that your organization depends on in order to function? Perhaps it’s something as simple as an email solution, or your productivity suite. If either of these stopped working properly, would you be able to sustain operations? What if your software licenses ran out and you lost access to them? These are some of the many pains of traditional software acquisition, and a new method of this can help you make significant headway in managing your organization’s technology.
Software as a Service is a great way to keep your business’s software dealings as painless as possible. By adopting such a model, you can avoid the high initial costs of software solutions, which can allow you to invest in other ventures that might otherwise be impossible. Just consider how much it costs to purchase multiple software licenses at any given time. Software as a Service is meant to provide your business a better way to manage multiple software licenses without any of the unfortunate side-effects. You might be surprised by the number of opportunities it provides.
Consider how often you have to upgrade your software licenses during your business technology’s tenure on its infrastructure. When your older applications grow outdated or unsupported, they become a hindrance to productivity and security. Therefore, your only real option is to purchase licenses for new software, a cost which is practically unavoidable in the traditional sense. Remember, it’s only a matter of time before you have to replace even the best software solution.
Software as a Service allows your business to pay a flat monthly rate per user rather than go all-in on licenses for multiple copies of the software. Think of it like this; you’re paying for access to full versions of software, rather than actually owning it yourself. It’s kind of like renting it. For example, the convenience and affordability of renting an apartment that you aren’t responsible for maintaining, rather than taking care of a full-blown home, is definitely something to consider when looking for housing.
There is no real reason not to consider Software as a Service for your organization–especially if you’re outsourcing it to a managed service provider. Since SaaS allows each of your employees access to important applications through the cloud, you’ll save both time and resources that are better spent elsewhere. You won’t have to install the latest versions of each required application on each workstation, which is invaluable in and of itself. Furthermore, it’s much easier to update cloud-hosted applications, as you apply the updates and patches in one place rather than several–although this likely won’t be a problem, as your SaaS provider will likely handle this responsibility for you.
Some examples of a cloud-hosted Software as a Service solution include a hosted email like Microsoft Outlook or other enterprise-level email solutions, or productivity suites like Google’s G-Suite or Microsoft OneDrive. Overall, you’ll be hard-pressed to find a reason not to implement SaaS. To learn more, reach out to us at (317) 705-0333.
Tip of the Week: Preserve Your Privacy With These 3 Websites

With the explosive popularity of social networking, the Internet seems to be a less private place than ever. With both communication and cyber crime rising in commonality, online privacy seems to be turning into a less attainable goal than ever. However, for this week’s tip, we’ll review some of the tools out there that can help you fight for your right to privacy.
Account Killer
How many email accounts have you accumulated in your life? How many do you still currently use? Chances are, the first number is much larger than the second, which means that you have plenty of potential vulnerabilities lying around for a hacker to find and exploit. Account Killer does exactly what it says on the box, allowing you to delete unused accounts and shore up potential vulnerabilities.
Have I Been Pwned
This website gives users an outlet to check if one of their online accounts has ever been involved in a cybercrime or breach event. By securely entering their email address, they can run a search of Have I Been Pwned’s database of nearly 4 billion compromised records to establish if any of their accounts may have been compromised, and which ones were. This one may be one to run periodically, as you never know when one of your accounts may have been involved in a breach.
DuckDuckGo
While it may have a questionable reputation, anonymous browsing has some uses for those doing a search online that they don’t want someone to see later. For example, anonymous browsing can enable you to search for a gift for someone else with access to the computer without fear of their discovering your activity. This variety of browsing can also land the lowest rates for airfare, as travel websites will often offer better deals when they are unsure where you are originally located.
At the end of the day, it is much simpler to avoid digital privacy issues than it is to fix them after the fact. After all, the Internet has a very long memory.
For more data security tips and best practices, keep checking in to our blog.
Google Instant Is Dead… Did You Notice?

Users can expect a change to how Google delivers results going forward, as the search engine has killed off its ‘Instant’ feature. This feature–introduced in 2010–influenced how results were displayed, and when.
With Instant, as a user typed in their query into Google’s search bar, Google would immediately start delivering relevant results based on what was typed thus far. These were different than the search suggestions, which would appear in a drop-down below the search bar. These suggestions are reportedly here to stay.
Google’s reasoning for removing the Instant feature was simply to better focus on making search work better on the wide variety of devices that Google is now available on. According to a statement from Google:
“We launched Google Instant back in 2010 with the goal to provide users with the information they need as quickly as possible, even as they typed their searches on desktop devices. Since then, many more of our searches happen on mobile, with very different input and interaction and screen constraints.”
In essence, so many users use Google on a mobile device that Instant no longer makes sense for Google to maintain. On top of that, many use the address bar of their browser to search, which also was incompatible with Instant.
All in all, this is just another example of how businesses of all shapes and sizes have to adapt to meet the needs of their users–even Google. If a user’s experience doesn’t meet their expectations, they are apt to be unhappy and seek another outlet that meets these expectations.
What do you think about this change that Google is adopting? Will it make a difference to your browsing? Let us know in the comments, and be sure to subscribe to the Catalyst Technology Group blog!
LeakerLocker Takes Exposure to New Heights By Sharing Your Mobile Browser History

Ransomware, the malware that locks down its victim’s files until they pay up, has always been a frustrating issue to deal with. However, a recent mobile ransomware will make the issue a little more personal… by sharing the victim’s mobile browsing history.
This introduces an important question: how much is it worth to you for your browsing history to kept secret? According to LeakerLocker, the answer is $ 50. This Android malware will steal the user’s browsing history, along with photos and videos from the device, any Facebook messages, and the user’s location history, all along with other sensitive information the mobile device has access to.
Admittedly, considering what many may have on their phones that they don’t want others to see, LeakerLocker utilizes a potent motivation: the fear of embarrassment. Think to yourself for a moment–do you have anything on your phone that you’d rather not anyone else know about?
LeakerLocker asks, is $ 50 enough to keep your secrets hidden from view?
Unlike many examples of ransomware, the researchers at McAfee have discovered that LeakerLocker seems not to encrypt any data. Rather, the ransomware allegedly takes a backup of all information on the infected device, which is then used to blackmail the owner into paying up.
This ransomware was spread via two Google Play Store apps, Wallpapers Blur HD and Booster & Channel Cleaner Pro. These fraudulent applications have since been removed. A major red flag for these apps were the incredible amount of permissions that LeakerLocker obtained through them. These apps requested the ability to both read and send messages, manage the device’s calls, and access the contact list. Once approved, LeakerLocker shuts the user out of the device and demands its ransom through the lock screen–and thanks to the access the user had just given the app, it can easily seem that paying the ransom is the only option.
However, there is no way of knowing for sure if LeakerLocker has actually accessed the data it claims to. Having said that, it has been confirmed that the ransomware can access the device’s browsing history, along with text and email messages, the device’s calling history, and yes, camera images.
As we recommend when someone is dealing with any form of ransomware, paying the ransom will almost certainly do you no good. Where’s the guarantee that the hackers haven’t scammed you out of the cost of your data, and that the money you’ve given them won’t finance their next heist?
If you have concerns with keeping your data secured and your business safe from threats like LeakerLocker and the many ransomware variants out there, reach out to us. We can help to make sure your network is as secure as possible, from the software all the way to the employees who use it. Call us at (317) 705-0333 for more information.
Tip of the Week: The Windows 10 Touch Keyboard Offers Considerable Utility

Digital communication has changed a lot over the years. Nowadays, special characters are commonplace for the modern person to communicate with. The special characters that are most frequently used are called emojis. They have become a staple in mobile communications, even among professionals. After all, who hasn’t responded to a message with an emoji thumbs up or a smiley face?
There are more special characters too, such as currency symbols, fractions, and more that enhance people’s ability to communicate. The problem is, that these symbols and emoticons aren’t located on the traditional keyboard. So Microsoft has added some pretty dynamic functionality into their Windows 10 operating system’s touch keyboard.
Windows 10 – Touch Keyboard
Before those of you using Windows 10 computers on a traditional PC with no touch capability get confused, these tips can absolutely be taken advantage up through use of the traditional mouse. If that is the case, you will need to access the onscreen keyboard on your Windows 10 device. The process for this is outline here:
- Right click a blank spot on your taskbar.
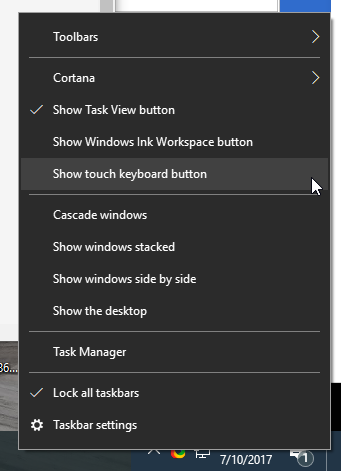
- Click Show Touch keyboard button.
- Touch keyboard icon will appear to the left of the time clock on your taskbar.
Primary Touchpad Keyboard
So when you are looking to add special characters, simply click on the touch keyboard icon and a keyboard that looks something like this will appear: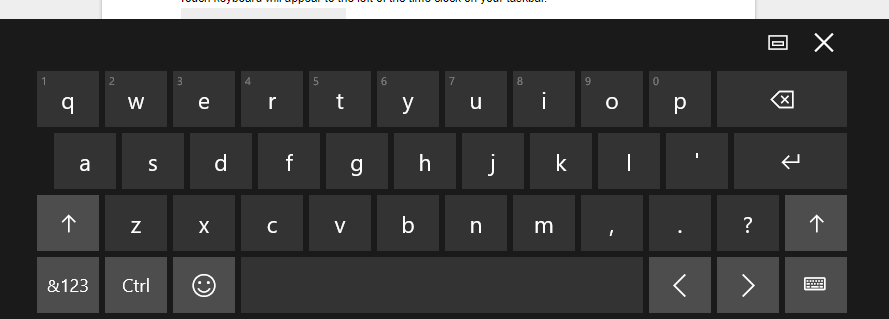
Related Characters
Outside of your standard keys, you have quick access to so much more. If you’re looking for a character that is related to one that is on the traditional keyboard, clicking and holding will bring up a menu of similar letters. For example, some Spanish conversations might require the letter: ñ. To find this, simply click the letter ‘n’ and hold it, as depicted below: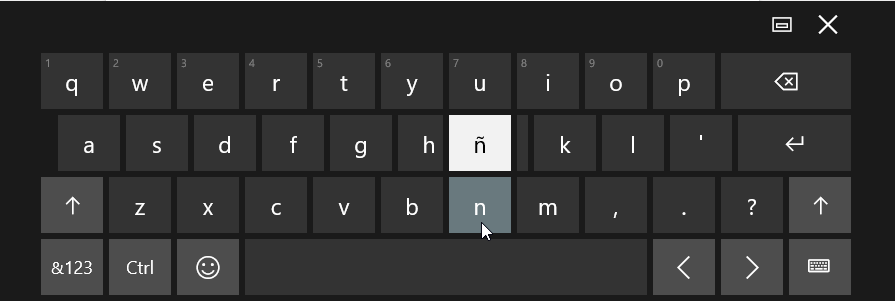
Punctuation and Numerals
For more characters, click on the &123 button on the bottom-left part of the keyboard. You can see this highlighted below. Once you press that, you can long-press and receive more options.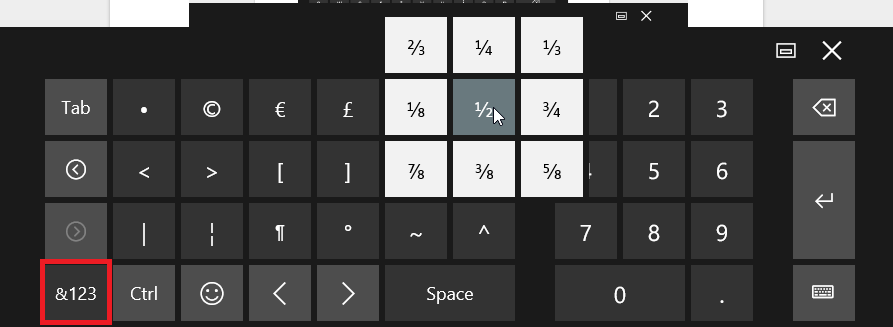
Emojis
Clicking on the happy face emoji will light your keyboard up with faces and other emoticons.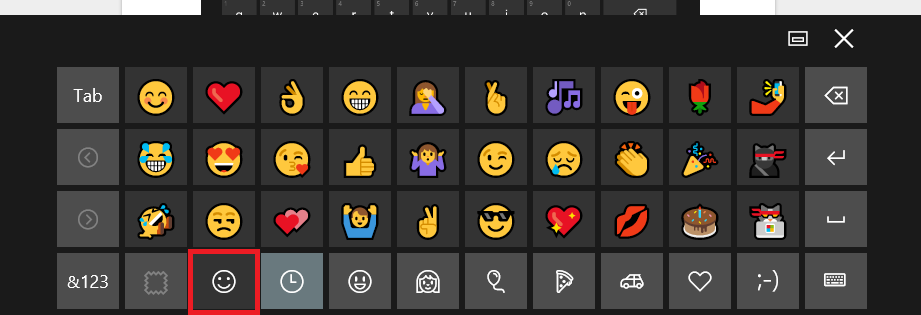
For the modern user, being able to creatively communicate is important. With Windows 10’s on-screen keyboard integration, it is now easier than ever to say exactly what you want to say. For more great tips and tricks, subscribe to our blog today!
The Good, the Bad and the Risky: Current State of IT Security for SMBs

Technology has revolutionized business. However, along with all the advantages and benefits technology affords us, it comes with a few risks and vulnerabilities that some businesses are still struggling to come to terms with. For example, storing records electronically makes them easier to organize and locate when they’re needed. It also makes them vulnerable to hacker and cyber-attacks. Still, most SMBs are working toward mitigating risks as opposed to abandoning the use of technology in their business operations – and a current assessment of the situation does show improvement over past years.
The following seven statistics examine the current state of IT security for SMBs, as well as why these numbers should be of importance to you and your business.
- Only 36 percent of organizations report being fully aware of employee activity on their network.
From terminated employees with continued access to your network to current employees spending the day on social media instead of working and even to Internet of Things devices connecting without knowledge or permission of a company, there are all types of unauthorized access that a business network has to be aware of. This study is saying that only 1/3 of companies have an idea of what is happening on their network. When it comes to network access, what you don’t know can hurt you – and cost your company money! - The percentage of businesses that that have at least some control over employee activity on their network grew from 62 percent in 2016 to 85 percent in 2017.
This statistic is one of the few significant positive changes that is highlighted in this business IT risk report. SMBs are finally starting to recognize the importance of access control when it comes to IT security. The truth is, many major security breaches are caused by human error (some of it intentional) from employees who access a network or parts of a network outside of their job with malicious intent. - 65 percent of respondents admitted to having security incidents in 2016; the most common reasons cited were malware and human errors.
SMBs are being targeted regularly by cyber criminals. Many of these respondents have failed to take the proper network security measures, despite a security incident. Historically, many SMBs are involved in a full-scale cyber-attack and experience loss before they fully enact and enforce network security. - 48 percent of organizations that have to comply with any cyber security standard still struggle to ensure continuous compliance and provide complete evidence of it to auditors.
Certain industries require SMBs to comply with cyber security standards and regulations, regardless of their size and network security experience. Moving forward, it will be more and more common for the entries requiring compliance to request proof of compliance, including policy implementation and compliance audits. For SMBs who can’t meet these compliances, it is recommended that they contact a third party, like Catalyst Technology Group for guidance. - 79 percent of respondents say that detecting and mitigating human errors, both malicious or accidental is critical for reducing IT risks.
The secret is out. Sometimes, humans make mistakes. Other times, they are just up to no-good. For example, malware may ravage a network as a result of an employee that accidently clicks on an attachment in their email. SMBs have started to acknowledge the element of risk generated on a regular base by humans. Businesses next need to take measures to mitigate the human threat with proper training of best practices, ensuring they take situationally-appropriate network security measures, and regularly update these measures to keep up with threats and risks.
These are just five of the many items that Netwrix Risk Report can tell SMBs about all of the threats that they are facing every day. For those of you who don’t have time to read IT risk reports, a partnership with Catalyst Technology Group will go a long way toward making your network and data safe – against all types of threats, including the human element.
Unified Threat Management Keeps Your Network Safer

Network security is equally important for businesses of all sizes. Ensuring that your infrastructure remains firm is one of the most crucial tasks in managing a business. You don’t have to do it alone, though. There are enterprise-level tools available that can give small businesses the same security standards as larger organizations, and it all starts with a Unified Threat Management (UTM) solution.
A UTM takes four of the best enterprise-level tools and combines them into one great package. You’ll have a firewall, antivirus, spam blocker, and content filter in place to keep your business secure. You’ll quickly discover that this is the best way to handle network security.
Firewall
Your firewall is the first line of defense for your network, tracking any incoming or outgoing data to keep threats at bay. If you keep threats from entering your network in the first place, you’ll decrease the likelihood of your business suffering a data breach or other similar attack. Granted, even the best firewall can’t keep out all threats, which is why the rest of the UTM is particularly important.
Antivirus
You might notice that most desktops come with a consumer-grade free antivirus, but this isn’t ideal for business purposes. It will only provide a minimal defense at best. Meanwhile, an enterprise-level antivirus solution can scan your system to check for any known threats on your network, including viruses, malware, spyware, and so much more. This type of tool is often the only way to find some of the more scrupulous threats on your network, so it’s a critical tool for any business that wants to take network security seriously.
Spam Blocking
Spam can be both a waste of time and a threat to your organization’s security. A single employee downloading the wrong attachment or visiting a malicious website could become a major problem for your business. Data could be compromised in the fallout, which could damage your organization’s reputation and subject it to compliance fines. The most effective way to protect yourself from spam is a proactive solution that keeps suspicious messages out of your inbox in the first place. You can’t click on messages that aren’t there, right?
Content Filter
The Internet contains practically endless threats, and if you’re not careful, they can find their way onto your infrastructure via your employees’ browsing practices. There is malicious content on the web that can install malware or infect your computer with viruses. Furthermore, some websites might try to farm credentials from your employees, including personal or sensitive information. A web content filter can block these websites from being accessed on your network, allowing you to keep employees from accessing unsafe or wasteful online content. Plus, it can be implemented on a per-user basis.
Is your organization’s network lacking proper security measures? If so, Catalyst Technology Group can help. To learn more, reach out to us at (317) 705-0333.
Tip of the Week: How to Clear Browser Cache in Chrome, Firefox, and Edge

Is your web browser running as well as it should be? Sometimes you might experience situations where your browser freezes or crashes. If your web browser starts acting up, you can troubleshoot what’s wrong by trying to clear the cache.
What is the Cache?
The cache is what stores data as you go about your business on the Internet. The cache doesn’t normally affect performance. After all, cookies and other such data don’t cause any notable issues. Your web browser’s cache generally consists of files from websites that you often visit so that your computer can load them faster. Visiting a website once will download all of the pictures and other graphical interfaces so that the next time you load the page, it won’t have to redownload them. Depending on the specifications of your computer, your cache might eventually accumulate enough data to affect its performance. If you’re having trouble with the cache, you might experience pages freezing, unfinished loading, and applications failing to respond.
Clearing Your Browser’s Cache
To solve these issues, you can clear your browser’s cache. This is sort of like hitting the reset button on your browser. We’ll list out how you accomplish this in the various web browsers that are at your disposal.
Google Chrome
In the browser toolbar, you’ll notice the three-dot icon. Click it and select More tools > Clear browsing data. Next, select the boxes for Cookies and other site and plugin data, as well as Cached images and files. You can then use the dropdown menu under Obliterate the following items from: to select the amount of data you’d like to delete. Once you’ve done so, click on Clear browsing data.
Mozilla Firefox
In the Firefox toolbar, select the three-bar icon and navigate through History. Next, select Clear Recent History. This brings up a new Clear Recent History window. From the dropdown menu, next to Time range to clear, select Everything. Under Details, check the box next to Cache, and click Clear Now. Once you’ve exited out of the browser, reopen Firefox.
Microsoft Edge
At the top-right corner of the screen, select the Hub icon, which is the three-horizontal lines. Click the History > Clear all history. Next, select Cached data and files. Once you’ve done this, click Clear. After you see the All Clear! message, close out Edge and reopen it.
Now that your cache is cleared, see if the browser’s activity has returned to normal. Some of your regularly-visited websites may take longer to load initially. This actually isn’t a problem–it’s just your browser trying to fill in some of the cache data that you just deleted. Once you’ve loaded the site a few more times, you’ll see its performance is much-improved.
If you’re still experiencing problems with your browser, perhaps the problem lies elsewhere. Unfortunately, it can be a bit tricky to nail down the cause without the assistance of a trained IT professional. If your organization is suffering from technical issues, reach out to Catalyst Technology Group at (317) 705-0333.

