Project Management Tips From the Pros

If you’ve ever managed a major IT project, you’re probably well acquainted with Murphy’s Law: “Anything that can go wrong, will go wrong.” Every project is going to have some rough patches. The key to overcoming these challenges lays not with the execution of the plan, but with the preparation. Here are four things to consider when you’re planning out your next long-term IT project.
Know Your Needs
Believe it or not, understanding exactly what your company needs from a project and translating that into a well-defined strategy with realistic goals may be the difference between a success and failure. First, it’s best to look at the big picture.
- What is the desired result?
- What does the project do for your business?
- How will the implementation of this project affect other departments?
- Will the project directly impact clients/prospects?
- Will there be any downtime?
- Does the team need to be educated about this project?
Budgeting for the Unknown
Prices go up. Projects get delayed. Accidents happen. More often than not, you’re going to run into an unplanned incident during the duration of your project. The best way to make sure that your budget doesn’t come up short is by anticipating that there will be unforeseen expenses. Whenever possible, it’s preferred that you give yourself a bit of ‘wiggle room’ within your budget. Of course, you can’t predict the future – but you can look to previous projects for an idea of what sort of snafus you are likely to encounter. Giving yourself a bit of cushion when planning out your budget might end up saving you big time down the road. And if it turns out that you didn’t need that extra money, then congratulations! Your project was completed under budget!
Determine Benchmarks and Measurements
Especially important during long term IT projects is figuring out ways to measure and gauge the project’s progress. You will want to determine a plan for these measurements before you begin the project. This will help you maintain forward momentum, keep your budget in check and show areas that need improvements for the next time you have a similar project. Key performance indicators (KPIs) are ways to measure that success. Keeping track of the following metrics will help you get a grasp on the way your project’s progress throughout the execution:
- Actual cost
- Cost Variance
- Earned Value
- Planned Value
- Return on Investment
Too often in a project’s execution, only the project managers will know how the project is fairing. Everyone else is only privy to the sections of the project that apply directly to them. Project managers are there to drive the project – and part of that is communicating with resources – both inside and outside of the project. For example, if your project is going to require your network to be offline, giving advance warning to those who will impacted by this downtime is not only courteous, but keeps your project on track. There is nothing like having to delay your progress because there was an important meeting scheduled for the time you had planned on bringing the network offline.
There are many programs and applications available to those who are looking for ways to improve organization and communication throughout your project. Project management software gives PMs a unified solution where they’re able to track inventory, budget, KPIs, resources and a whole host of parts of a project in motion.
As with most things in life, projects rarely go as planned. The only thing that a project management team can do is make an effort to plan ahead, anticipate needs, and be ready to face whatever challenges are thrown their way. Do you have an IT project in mind but are unsure of how to manage and execute it? Contact Catalyst Technology Group today at (317) 705-0333.
3 Ways Managed IT Can Prevent Technology Troubles
![]()
Is technology a major problem for your organization? If so you’re just like many small businesses out there that think they can’t afford proper IT maintenance and management. Thankfully, managed services threatens this misperception by bringing affordable preventative solutions to the table.
Outsourced IT, or managed services, can be a valuable investment for a business that wants to prevent problems from occurring rather than react to them as they happen. By effectively using managed IT, you can significantly reduce the risk of your technology failing before it’s meant to.
A Network Assessment
Before you can work toward resolving problems found on your network, you need to know that they exist. This is where a comprehensive network assessment comes into play. A network assessment shows you where your network has its flaws, whether they are traffic bottlenecks, security vulnerabilities, or even just failing hardware components. A third party like Catalyst Technology Group can provide this service for you so that you can get a clear, unbiased opinion on what you must do to improve your organization’s operations.
Remote Network Monitoring
Knowing what’s wrong is only half of the battle, though. Once you know where to look, you need to keep watch over your network to ensure that the weak points don’t develop into major problems. Yet, your in-house team likely doesn’t have time to monitor your entire infrastructure day-in and day-out. An outsourced IT provider like Catalyst Technology Group is far better suited to this role, as we can do so remotely without an on-site visit. We can then ensure that any maintenance that must be performed can be done before your network is put at risk.
Unified Threat Management
To keep your business from falling victim to a rogue virus or malware on your network, you need to take preventative measures. One of the best ways you can protect your business is with a Unified Threat Management solution, which provides the collective might of enterprise-level security solutions, including a firewall, antivirus, spam blocker, and content filter. By keeping threats like ransomware, Trojans, spyware, viruses, and so much more out of your infrastructure, you can prevent problems from happening in the first place.
Ultimately, managed IT that keeps issues from happening in the first place saves your business time and money. You can focus on making sure your business runs properly without interruptions. To learn more about managed IT, reach out to us at (317) 705-0333.
In The Wake Of A Disaster, Beware Of Charity Scams

Wanting to give donations in the wake of a disaster is admirable. However, with so many regions of the United States having been devastated by a natural disaster in recent weeks, there are dozens of illegitimate charities out there looking to take advantage of your generosity and compassion.
With resources like web pages and applications that allow donations to be collected via electronic payment, it’s easier than ever for fake charities and other bogus relief efforts to look, sound and feel legitimate. Here’s how to make sure that your donations are going to reach those in need.
- Stick with Charities You Have Known About: There are people that begin purchasing URLs for hurricanes or storms as soon as the list of that season’s storm names are released by the NOAA. When in doubt, choose an organization that you’re familiar with if possible.
- Evaluate Validity of Organizations: When you are trying to find a worthy charity or cause, you should always double check to make sure that they are who they say they are. These links are for a few websites that evaluate charities for legitimacy: Charity Navigator, Charity Watch, GuideStar, or the Better Business Bureau’s Wise Giving Alliance.
- Don’t Click on Links: Beware of any unsolicited links or attachments because they might be malware. Hackers love natural disasters because it’s an ideal time to use malware to exploit those in need.
Would you like to donate to a disaster fund? FEMA has a website that tells you how you can volunteer and/or donate responsibly. The National Voluntary Organizations Active in Disaster is also a great resource to find out how you can help without being scammed!
Artificial Intelligence: Right For The SMB?

If the results of a Google search for ‘small business technology trends’ is any indication, artificial intelligence (AI) is not something that just concerns larger businesses and enterprises. Judging by the sheer number of articles that have been produced over the last several months, it is easy to see why a user might get the impression that SMBs who are not considering (or that aren’t already) investigating possible uses of AI are detrimental to their own success.
For those of you who are unclear as to what exactly artificial intelligence is in the modern business setting, it should be noted that AI isn’t necessarily like traditional notions of Skynet from the Terminator series or Agent Smith from the Matrix. The AI we’re referring to hasn’t shown the ability to operate autonomously or made plans to eliminate humanity… at least not yet.
Rather, today’s version of AI is more of a way that computers can learn and solve problems based on information amassed in an extensive database. For example, AI might be referring to an application’s ability to understand human speech, take that audio and use it as data to more accurately predict a future purchase based on that audio, as well as, past purchases, buying behavior, demographics and other data. As the database grows, so improves the AI useable with that data.
- Machine learning – It means that technology uses data collected over time to make better predictions about what you want. The idea of machine learning is not like human learning. It still requires data to be input in some way. This technology is by no means brand new but it has really taken on a new life in recent times.
ex. Amazon uses your purchase history and the history of those similar to you to better advertise and recommend you products. - Deep learning – Machine learning that is enhanced by additional layers of data to further refine predictions making it more accurate as additional layers are accumulated.
AI Already in Use
Virtual personal assistants, like Apple’s ‘Siri’ and Amazon’s ‘Alexa’, are used by millions of people. The majority of those users haven’t realized that they’re already relying on AI. Asking Siri a question and having her answer is an example of machine learning. With each edition of these VPAs, capabilities and features are improving, expanding AI abilities with each release or update. How about Netflix? The popular film/TV application uses machine learning to try and curate content of media that you’re likely to enjoy.
AI and SMBs
Moving forward, your company will likely be met with inquiries regarding whether or not you’ve considered looking into artificial intelligence to improve operations, better accommodate customers, remain competitive with your peers who are considering AI, or any host of perceived benefits for SMBs. An investigation into AI use for an SMB can be something as simple as thinking of ways to automate processes or service customers better using technology. It’s worth noting, however, that before you can even think about using AI to bring your business to the next level, you’ll want to be cognizant of the fact that without advanced technology to handle it, exploring the use of AI is a moot point.
Software and Application Development
Those SMBs who are curious about possibilities but have neither the time nor budget to consider exploring AI for their own use should consider that their line of business application might already be exploring AI use. Which means that even though your SMB is not going to take any specific steps toward vetting and using AI in your business model, you’ll still reap the benefits of what it has to offer.
Far from the AI of Hollywood science fiction, today’s businesses are continuing to find new and innovative ways to apply AI to business intelligence and growth strategies. While small businesses might not have the capital to form their own AI exploration committee, there are still plenty of ways they can use AI to benefit their company and its clients. Are you interested in experimenting with AI? Connect with us at (317) 705-0333 or let us know in the comments below!
100 Countries Hit By Android DDoS Malware

In what is one of the first attacks of its kind, a botnet dubbed WireX swept across 100 countries, controlling over 120,000 IP addresses at its peak. The factor that made WireX so unique was the fact that the botnet was made up of Android-powered devices that had one of 300 malicious apps downloaded from the Google Play Store.
How It Works
WireX was designed to use HTTP requests to bombard their targets, directing as many as 20,000 requests to a target every second to use up the target’s server resources. This number of requests may not have been effective, if it weren’t for where WireX would direct its attack on the victim site. Rather than just sending 20,000 requests every second to the website as a whole, WireX would target specific pages that used more of the site’s resources. Search pages were frequently targeted for this reason.
Why Is WireX So Nasty?
There are a few factors that contribute to why WireX managed to cause such a big fuss, so quickly.
First off, although WireX is an Android-powered mobile botnet, the traffic it sends to the targeted website appears to be regular mobile browser traffic. This is a problem, because most experts who focus on defending companies from DDoS attacks utilize filters that help them to sort the malicious traffic out from the legitimate traffic. This is more difficult with WireX, as it includes its own fully-functioning browser that hides its information from the targeted system.
In addition to this, WireX also leverages SSL as a part of its attacks, which usually protects an Android user’s browser session. In this case, however, it only makes WireX more difficult to detect.
Defeating the DDoS
It ultimately took a team of experts from Cloudflare, Akamai, Flashpoint, Dyn, Google, Team Cymru and EiskIQ to stop WireX. The seven companies needed to pool their resources and data on WireX in order to identify it as a mobile-based attack, and then to identify the 300 malicious Google Play Store apps that delivered it. While these apps have not been named to the public, they were often media players, ringtones, or storage managers. Google has since blocked these apps from the Play Store, and has also removed them from the devices that were infected.
So, What Can You Do?
Your most effective defense against threats like WireX and other applications that sneak in malware is to simply not download applications that you don’t trust, as well as to educate employees on why they shouldn’t either. For more information on the latest threats and how you can protect yourself, call Catalyst Technology Group at (317) 705-0333.
48 Vulnerabilities Resolved On Patch Tuesday

Microsoft’s monthly Patch Tuesday issued resolutions to 48 vulnerabilities in August, including 15 that affected Windows, 25 critical flaws, 21 important flaws, and 27 that allowed for remote execution. This is a lot to consider, but the main jist of this is that lots of threats were fixed, and that your organization shouldn’t risk not implementing them as soon as possible.
Only 15 of the vulnerabilities affected Windows itself, but the others addressed issues with other Microsoft products, including Internet Explorer, Microsoft Edge, SharePoint, SQL Server, Hyper-V, and Kernel. Yet, only two of these flaws affected every single version of Windows and Windows Server, and none of them were being exploited in the wild by hackers.
One of these vulnerabilities demands your immediate attention, though, and that is the one that has your Windows Search feature in its crosshairs. This vulnerability, coded by Microsoft as CVE-2017-8620, can use the Server Management Block (SMB) to remotely control a system, be it a Windows Server unit or a Windows workstation. Since the flaw isn’t located in SMB itself, it isn’t affected by other threats like the notorious WannaCry ransomware and NotPetya.
This Windows advisory claims that the vulnerability takes advantage of the way that Windows Search works with objects in memory. A hacker can send customized messages through the Windows Search function to change user permissions. They can then take full advantage of their permissions to install, remove, or change applications on any infected device. They can also view, change, or delete any data that’s stored on it, or create a new account just for them with full administrator privileges.
A vulnerability like this is exactly what a hacker wants. They can basically take full control over a victim’s computer with minimum trouble. If you implement patches and security updates as they are released, you shouldn’t have anything to worry about. Does your business have an organized approach to implementing security patches? If not, there are solutions available that you can use to keep security at a maximum.
Outsourced IT often includes remote patching and maintenance that can be used, even by small businesses. Even better, it does this without costing your business an arm and a leg. Enterprise-level solutions are often the only way for your business to thrive in a world filled with competition, but that’s because they provide a significant benefit to your organization that you can’t afford to ignore. We can improve your network security in the same way as an internal IT department, but without the costs associated with adding new salaries to your budget. Catalyst Technology Group can help your organization implement new security solutions like remote monitoring and maintenance. To learn more, reach out to us at (317) 705-0333.
Tip of the Week: Improving Outlook With Three Tips

Does your business use Microsoft Outlook as its preferred email client? It’s likely that you have already noticed how dynamic of a solution it is for your business purposes, but little do you know that the most recent version of Outlook is stacked with some of the best features out there to make your user experience even better.
Here are three of the best ways you can use Outlook to get more productivity out of your workday.
Quickly Access Your Inbox
If you want to access your inbox without going through all sorts of folders or icons, you can easily do so with just a few keystrokes. Just press the Windows key and R, and you’ll open the Run window. Just type outlook into the field.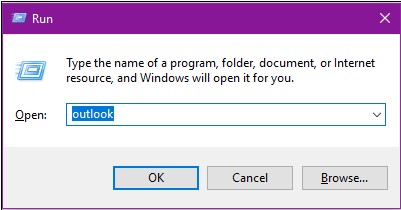
Add an Attachment
If you’ve worked in Excel or Word on a document, or recently downloaded a PDF or image file that you want to attach to an email, you can do that easily with Outlook. Outlook pulls any documents that you’ve recently opened and allows you to quickly attach it to a message.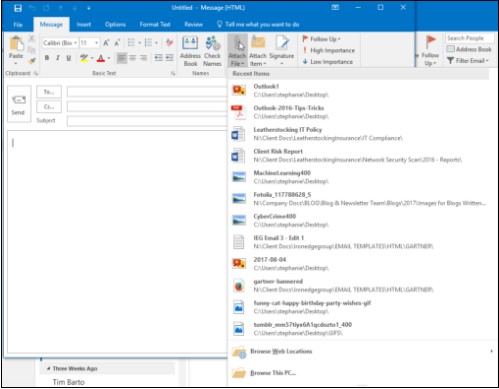
Deleting and Archiving
If you delete a file, it will be sent to your Delete folder. Delete folders are emptied from time to time, and once they have been emptied, the emails will be gone for good.
If you archive a file, it goes to the Archive folder. Archives messages will be removed from your inbox, but will keep them stashed away for later viewing. You can even set your emails to auto archive so that you don’t have to worry about doing it manually.
For more great tips and tricks about Microsoft Outlook and other Microsoft services, subscribe to the Catalyst Technology Group blog.
Network Security Needs To Be A Team Effort

Network security is more than just a conscientious attempt by your staff to protect your organization’s digital assets. It’s making sure that your employees know how to handle dangerous situations, implementing preventative IT measures to eliminate potential issues entirely, and having the right technology experts on-hand to handle tough problems that can’t be solved by a few pieces of technology.
To begin, let’s take a look at what role your organization’s IT department plays in the overall security of your business’ infrastructure. We’ll then move on to how the average employee can reinforce network security, and how outsourced help can be beneficial.
Your Internal IT (If Any)
First, the responsibilities of your IT department must be considered. Ordinarily, your IT department would be responsible for tasks such as monitoring your network, installing patches and security updates, and general upkeep of your technology systems. Of course, that assumes that you even have an IT department in the first place, which not a lot of small businesses have. The expense of hiring in-house technicians can add quite a bit of strain to your budget that you may not be able to afford. Or, worse yet, you leave all of the technology-related maintenance to your ordinary employees who have other jobs and responsibilities. This not only takes time away from your business’ busy employees, but also compromises security, as tasks may be rushed or performed wrong entirely.
What Your Employees Can Do
Even if you do have an internal IT department, your employees can practice certain security practices to ensure that they don’t contribute to your business’ troubles. Many issues concerning network security are caused by user error, such as clicking on the wrong link or downloading the wrong attachment. Furthermore, passwords–one of the most critical parts of any security protocol–are often created in such a way that they aren’t secure enough. Passwords should be long and complex, utilizing combinations of both upper and lower-case letters, along with numbers and symbols. They also shouldn’t be the same across the organization, or shared with others. Reinforce that your employees also be wary of any suspicious messages in their inboxes, and advise them to report anything strange or out of place to your IT department.
What You Can Do
Even if you do have an internal IT department, they might be so swamped with work that they don’t have the time to reinforce your network security. On the other hand, if they are dedicated to ensuring the security of your network, they may not have time to deal with the more routine tasks, like assisting with technology troubles or help desk support. Outsourcing your security, as well as general maintenance for your infrastructure, is a great way to assist your internal team with day-to-day responsibilities. Think of it as a way to resolve any bottlenecks that they may be running into, be it a lack of time to properly monitor your network security, or a lack of availability to resolve in-house employee technical difficulties. It’s just one way that outsourced IT solutions can help your business protect itself in the long run.
Does your organization need assistance with IT security? Catalyst Technology Group can help you augment your security capabilities through the use of managed IT services. To learn more about how we can keep your organization secure, reach out to us at (317) 705-0333.
It’s Silly Not To Ask These Important IT Questions

While being tech-savvy is much more commonplace than it used to be, asking a question about IT can still make one a bit nervous. This leads to many who are somewhat unlearned in technology feeling that they will be mocked for asking “dumb” questions. Well, fear not–we’ll explain some of the more common questions you might want to ask about technology.
We’re talking about what being “up to date” means in the world of technology. Often times users might ask questions such as “Why is your operating system’s version important,” or “Why does it matter if I have Windows 10 or not?” Other times, it will be used in the context of the technology being “updated” to protect against potential security troubles. Even more puzzling might be the term “patched,” which you may have thought was something you did to a piece of clothing that has seen some wear and tear.
Let’s examine some of the most common IT questions that people ask.
Why Is My Operating System Version Important?
It’s ideal to be using the latest version of your device’s operating system. By this, we mean the software that allows your devices, like smartphones or workstations, to be secure and useful–be it iOS, Windows, Android, Windows Server, or otherwise. That being said, the sad reality is that this is unlikely due to budget constraints and other complications. At the very least, be sure to keep your PCs and servers running operating systems that are still being supported by patches and security updates. These important updates resolve flaws that can place your device at risk of a hacking attack. Systems like Windows XP, Windows Vista, Windows Server 2000, and any of their predecessors have reached what is called the End of Life event, where they no longer receive updates or security fixes. Even just one of these machines on an infrastructure could put your business at risk. We can guarantee that the upgrade to a more recent OS is much cheaper than being hit by a threat such as malware or other security breaches.
How Do Security Patches Assist with Network Safety?
Even the most recent operating systems will have vulnerabilities that need to be fixed…eventually. Throughout the lifespan of your business’s technology, hackers will uncover vulnerabilities that can be exploited to steal data and so much more. Developers will issue patches and updates to resolve these. It’s a vicious cycle–hackers try to outdo security companies and developers at all times, while it takes everything that security companies have just to keep the constant threat of a data breach at bay. It’s your responsibility to make sure that all of this effort to keep you safe isn’t for naught by implementing them as they are released.
How Important is Data Backup?
Data backup is an important part of sustaining your business. Your data might be the only thing keeping you in the game following a disaster. Businesses have started to rely on digital records, updates, communications, payments, storage space, invoices, accounting, and much more–all in an attempt to simplify operations. If you were to lose all of the progress you’ve made on a six-month project in the blink of an eye without data backup, chances are you’ll be having a rather upsetting conversation with someone your business deals with, be it an angry client or a negligent employee.
Why Does it Matter Where Backups Are Stored?
If you store your backups in the same location as the rest of your data, they could both be wiped out by an unexpected event. Even if it’s not stored on the same device, but rather, the same infrastructure or network, this could be problematic. What if a disaster is capable of ending your business’s physical presence in the world in a matter of moments? A fire or tornado isn’t going to spare your server. Therefore, you need to keep it backed up at all times so as not to lose everything in one fell swoop.
Remember, there are no stupid questions when it comes to your business and IT. If you need some questions answered, reach out to Catalyst Technology Group at (317) 705-0333.


