What Every SMB Should Know When Selecting an IT Service Provider

Identifying a qualified managed service provider can be challenging–especially if you don’t know what to look for. You should be able to gauge the worth of an IT provider based on a couple of key qualifications, just like you would if you were selecting an employee. What are some of the primary features that you want to look for in a managed service provider?
Industry Experience
For any employee or organization that you deal with, you’ll want to hire only those who have some sort of industry experience that they can call upon. In this case, you’ll want your MSP to have some sort of information technology background so that they know how best to handle your business’s technology solutions. There will always be experience and knowledge that only comes from hands-on experience, so be sure that your prospective IT talent has some to spare.
Quicker Response Times
Have you ever dealt with an IT provider or a technician who doesn’t know the definition of acceptable response time? You always want your technicians to acknowledge when work needs to be done and to complete it within a reasonable timeframe. Time-wasting IT resources don’t provide much value for your organization, and the same can be said for your employees. It might sound cliche, but time is money, and you want the resources at your fingertips who can best manage it.
Scope of Service
You should consider how well-rounded your managed service provider is. What kind of services do they offer for your organization? You’ll find that a managed service provider that’s good for multiple solutions is much more efficient and useful than one who specializes in only one topic. You need to find your business an MSP that can handle a wide range of subjects ranging from network security to disaster recovery, and everything in between.
On-Site Services
Most issues can be resolved without an on-site visit, but you should still insist on a hands-on approach from time to time for more intensive tasks. Your MSP should be willing to make the trip to the office to ensure that they can do their job properly. After all, it’s difficult to get any hands-on work done while not in the office–especially if it’s diagnosing a particular hardware issue that needs an on-site visit to address.
Does your business need help with technology management and maintenance? Reach out to Catalyst Technology Group at (317) 705-0333, your local and reliable managed service provider.
These Gifts Can Come with Security Issues

The holiday season is coming to a close, with meals shared and gifts opened. You may have even received a new gizmo or doodad that you’re looking forward to trying out. Not to burst your bubble, but there is unfortunately a chance that the gizmo you had hoped to get (or purchased for a loved one) may lead to a security breach.
Smart Home Hubs and Assistants
These devices were touted as useful gadgets to have around the house as a mix between a media center and reference source. The trouble with devices like these is that they are always listening for you to speak, with microphones that automatically activate. Think about everything you say in the privacy of your own home. A cybercriminal could listen in, taking that privacy away and quite possibly learning some invaluable information.
To make this situation worse, many “smart home” devices also have cameras, invading your privacy in yet another way.
Admittedly, the thought of controlling one’s house by telling it what to do is, for lack of a better term, pretty cool. However, the questionable security that many of these devices suffer from gives cybercriminals the unique opportunity to spy on you, whether you use the assistant at home or in the office. This is also important to keep in mind if a young person you know recently received one of these devices.
Smart and Connected Toys
While many connected devices are clearly meant for an older demographic, there is an equal amount that are intended for children. For example, many toys are now capable of functioning in a way quite similar to a smart home hub, and others have features that are outright creepy. For example, if a child has a Toymail Talkie, a cybercriminal could use it to communicate directly to that child. Other connected toys offer cybercriminals with intimate details about the schedule of a child. For instance, the connected bath toy, Edwin the Duck, can be used to tell a hacker the general time that a child is in the bath and when they are put down for the night.
Connected and Smart Appliances
Grown-ups have to have their toys, too. Appliances and accessories with “smart” capabilities are becoming increasingly common, but unfortunately lack the security required to protect them from cyberattack and intrusion. Assorted wearable tech, like fitness trackers, and Internet of Things devices, or any of those devices that aren’t a computer or laptop but still utilize the Internet, are becoming more and more popular. Unfortunately, because their security is sub-par, these devices can easily be leveraged as a part of a botnet, or can also be used to extract data from their surroundings.
DNA Tests
It would seem that there was a sizable push to frame these ancestry testing kits as the perfect holiday gift this year, despite there being host to numerous privacy issues. Consider what you have to provide to the company. By handing over a vial of your spit, you’re giving them the most unique piece of personally identifiable information you possess: your genetic code, also known as your DNA.
This information quickly becomes very valuable once the topic of research is brought up.
When using one of these services, there are plenty of agreements to sign. These agreements will often give the company the leeway to use your genetic data as they please, including selling a digitized version to whomever is willing to pay.
Despite the Genetic Information Nondiscrimination Act of 2008 forbidding the use of genetic information to justify discriminatory acts, like firing someone because they have a predisposition to a medical condition, it isn’t easy to prove this kind of discrimination. After all, an employer could easily find some other reason to terminate someone’s employment–the fact that they were predisposed to a medical condition that would keep them out of work would just be a “coincidence.”
While we hope that your holidays were as bright and cheerful as they should be, we don’t want an unexpected data breach to spoil those memories. For more products that could put your security at risk, check out Mozilla’s handy guide.
Did you have any of these items on your wishlist? Is it worth keeping them around despite the risk to your data security? Leave your thoughts on the matter in the comments section!
As Technology Has Evolved. So Have Our Holiday Traditions

Merry Christmas! We know that for the small business owner, even on Christmas day, business doesn’t completely stop. Sure you can spend time with loved ones and take a couple days off from the grind, but tomorrow is another day. According to one study, people are gifting technology more than ever, so much so that new traditions that include technology, are replacing the once-held notion that technology was a distraction.
The survey called “Happy Digital Holidays: Technology, Culture and Emerging Holiday Tradition” has highlighted just how the holiday season is being changed by technology. This whole concept is not that surprising. Consider how much technology has become a part of our lives in recent times, and how much we typically rely on it; not to mention how eCommerce has changed the way people buy and receive goods (especially around the holidays).
From communicating and managing busy schedules, to the content consumption that has helped define an entire generation, technology is a static part of people’s lives. The surprising aspect of this for many, is that technology isn’t just being used more by everyone around the holidays, it is being integrated into typical holiday traditions. Some statistics include:
- More than 22 percent of men keep a family calendar to track the holiday activities
- More than 40 percent of people use social media to keep track of holiday events
- Around one of four people will use video calling in lieu of the phone
- Over half of people use social media to keep in touch with friends and family
- Over half of drivers use map applications that run on GPS technology to get to their destinations
- Over 10% of people will send virtual gifts this Christmas
As technology becomes a larger part of everyone’s life, and people don’t have the same amount of liberties to take time off from their regular tasks, expect to see technology become a mainstay in new Christmas traditions.
Has your family developed any new traditions with the use of new technologies? Let us know in the comments section below. From all of us at Catalyst Technology Group, have a very merry Christmas!
Tip of the Week: Cortana Can Do Even More than You Might Realize
One of the most recognizable names in technology isn’t a person, it’s a virtual assistant: Cortana. While Cortana has been of great use to many users, sometimes that user isn’t actually the person who owns the device and is just someone else in the same room. This can be annoying, but there’s a way to acquaint Cortana with a single user’s voice and listen to them exclusively.
To set this up, you’ll need to access Cortana’s Settings. First, click on the Cortana Icon that appears on the taskbar.

Next, access the settings menu for Cortana by clicking on the gear icon in the Cortana window that appears.
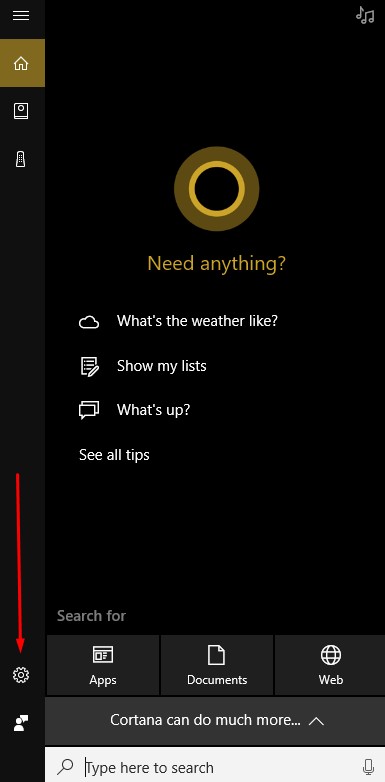
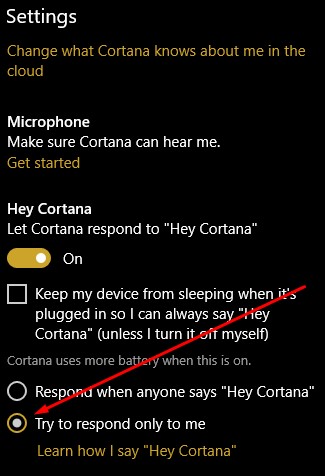
Activate Let Cortana respond to “Hey Cortana” and select Learn how I say “Hey Cortana.”
Once you do so, you will be prompted to recite six phrases so that Cortana can establish how you will say “Hey Cortana.”
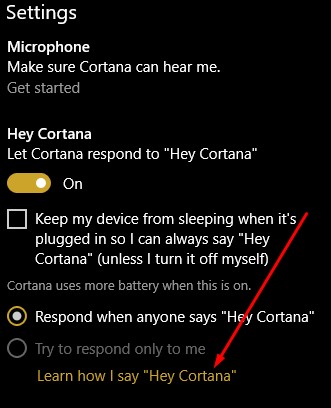
After this exercise is completed, go back to Cortana’s settings and confirm that try to respond only to me is selected.
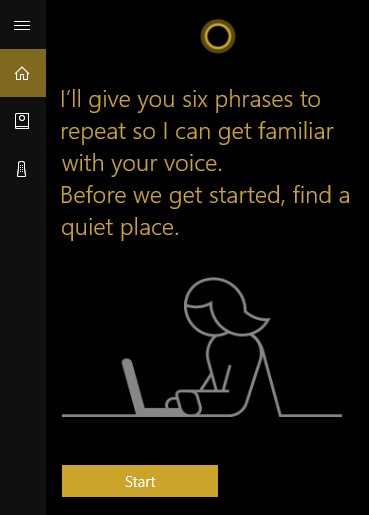
Cortana is now primed to listen to only you and you can now use it for many purposes, including to navigate Windows 10.
Are there any other assistants you use, like Alexa, the Google Assistant, Siri, or Bixby? Which one is your favorite? Tell us why in the comments section!
Investing in Innovative Network Security a Must

In 2018, enhancing cybersecurity has to be at the top of every business owner’s to-do list. If your business relies on Internet-connected computing at all, you need to invest, and invest wisely in innovative security constructs. Fueled by demand, organizations from around the world have made a point to protect themselves, their data, and their customers’ personal information against some of the most sophisticated threats ever created. They’ve done so in many ways that include utilizing cloud computing, biometric identification and authentication, security analysis, and managed security services.
There is more to it than throwing money and time at the problem. Here is a comprehensive list of some of the ways organizations from around the world have prioritized cybersecurity.
- Education and training – By training your staff on the fundamentals of cybersecurity, you are doing your company, your vendors, and your clients a big favor. They just may take some of what they’ve learned and use it for their own protection. Understanding the risks that are prevalent today, will help your business see tomorrow.
- Prioritize risk management – Making risk management, that is in this context the action of mitigating risk brought by threats that include software vulnerabilities, hacking attacks, and malware, a management-level responsibility makes cybersecurity governance an organizational priority.
- A multi-layered security approach – By tracking the movement of data out of your network, and prioritizing the protection of said data, you also protect the architecture that runs on that network.
- Threat monitoring and sharing – Sharing threat data with vendors, clients, and other entities, can have a positive effect on your organization’s ability to mitigate risk because, by-in-large, those organizations will share the threats they encounter with you.
- Effective breach response – With the use of innovative tools that include enterprise firewalls and spam filters, the moment a breach is reported, a breach response plan will eliminate the danger quickly and quarantine any data that shows any sign of corruption.
- Testing – Routine penetration tests to the network, as well as staff breach awareness tests can go a long way toward limiting your organizational exposure to cyber threats.
Innovative solutions and practices to ward against malware and other threats are essential for today’s business, and can endanger you company if not made a priority. To learn more, reach out to us at (317) 705-0333.
The End of Your OS’ Life and Your Next Move

Software developers create software for function, to make profit, to challenge convention, and many other reasons, but when a software company becomes as important to people as Microsoft has become, they have to ensure that their products are well supported. Microsoft support, as an extension of their software offerings, typically helps users navigate the problems they have with their software. Every so often, however, the product you have navigated automated menu after automated menu for will turn out to be unsupported, leaving you asking yourself, “When did that happen?”
Microsoft is unlike many other software developers, of course. Their software runs a majority of the business computing infrastructures in the world; and, as a result, they continuously update and support their programs for years after launch. They have to. Too many people depend on the software they develop to leave them unsupported. A problem is presented to businesses that don’t know that their software’s end of support dates are coming up. These businesses are in danger of either running systems that depend on unsupported software; or, spending significant capital on upgrading to a more current, and reliable computing construct. Windows 7 and Windows Server 2008 R2 are the next two titles on tap for obsolescence, losing support after January 13, 2020.
Planning for the long term and knowing what your options are can put any organization in an advantageous position. At Catalyst Technology Group, we are dedicated to ensuring our clients are in the know and ready to pounce on any opportunity they have to improve their business. In this case, getting out from under unsupported software, and antiquated hardware. With the end of support date for two of Microsoft’s frequently-used operating systems on the horizon, here are three options your organization has to ensure that, before the time comes, you’ve moved onto circumstances that won’t permanently damage your business’ ability to conduct business.
Update Everything
If your organization has the capital to upgrade your in-house server and software, there is no real downside to doing so. If you host your own hardware now, but run some semblance of Windows Server 2008, there is a good chance that the hardware you run it on is “old”. Older hardware has older components that are naturally more prone to failure than newer components. At Catalyst Technology Group, we can migrate all of your files to new hardware that runs software that is in no danger of being unsupported like Windows Server 2016. We can also upgrade and managed all of your organization’s software. Despite its popularity and effectiveness, Windows 7 will have to be upgraded to Windows 10 as Microsoft has stated that they will be standardizing the Windows platform and be making frequent updates to Windows 10 for the foreseeable future. This option will also cost the most, as buying new hardware is an extraordinarily expensive endeavor.
Completely Virtualize
Another option that the modern business has is to virtualize all of its data and hardware and host their company’s infrastructure in the cloud. Utility computing in the cloud is commonplace today for businesses of all kinds user needs. In fact, your business probably already takes advantage of it on some level. On this large of a scale, however, where everything is virtualized, you need to come in with a plan. The IT Professionals at Catalyst Technology Group can provide you with a detailed roadmap that properly take into account your organization’s situations. Essentially the relationships we’ve established over the years will help your organization quickly move its computing infrastructure to the cloud, providing enhanced accessibility, flexibility, and mitigating the need for you to make outrageous capital investment.
Build a Powerhouse
For companies that aren’t comfortable hosting all of their data and infrastructure in the cloud, there is a powerful solution: to build a hybrid cloud. There is a misconception out there that all cloud interfaces are hosted in faraway data centers. Any organization can build a powerful, reliable, and sustainable cloud computing platform on premises that allows you the best of both worlds: a flexible, accessible computing construct that is available from anywhere there is an Internet connection, on any device; and, one that is hosted in your office, managed by people you trust, and as secure as you want it to be. Catalyst Technology Group technicians can design and implement any strategic hybrid infrastructure platform your business could need. For companies that are tasked with federal and state mandates, the hybrid cloud solution is a great way to maintain the security and reporting necessary, with the collaborative options of hosted utility computing.
Microsoft isn’t the only software company dumping support for old software, but since over 90% of the computers in the world run some semblance of Windows, it is important to understand just what you are up against if you do not get out in front of Microsoft’s decision to stop support early in 2020. Organizations that choose to go this route will need the expertise that only professional IT technicians have. At Catalyst Technology Group, our technicians have experience with server migration, public, private, and hybrid cloud roll-outs, and working with hardware and software vendors to get our clients’ computing infrastructures up and running the way the need them. To learn more about the end of support dates for Windows 7/Windows Server 2008 R2, or to talk to one of our IT professionals about where your organization should go next, call us today at (317) 705-0333.
Tip of the Week: Using Excel to Excel-lerate

Microsoft Excel has been around for quite some time, but it’s one of the trickier Microsoft Office solutions to master. You might know all about some of the more common Excel tricks, but do you know these power shortcuts that can help you fully take advantage of the spreadsheet software? Here are some obscure Excel shortcuts that your organization can take advantage of.
However, before we jump into any new keyboard shortcuts, we want to remind you that all of the basic keyboard shortcuts that work in other Microsoft products will still work here. All of the tried and true shortcuts like Copy, Cut, Paste, and Find, will all work here in Excel.
Check Specific Formulas
Excel doesn’t default to showing you the formulas in your cells. Instead, all it will show you is the result of the formula. If you click on a cell, the formula will appear in the formula bar at the top of the spreadsheet. Doing this for each and every one of your cells can be troublesome and time-consuming. You can toggle your spreadsheet between values and formulas by using the Ctrl + ` keyboard shortcut.
Border Your Cells
If you don’t want to waste a bunch of time by finding specific borders for your cells, you can use the default one by pressing the keyboard shortcut for Ctrl + Shift + 7. This surrounds the cells you’ve selected with a simple border.
Remove Cell Borders
To quickly remove borders from your cells, you can use the keyboard shortcut for Ctrl + – (minus). It’s a quick solution to fix borders that didn’t turn out the way you wanted them to.
Select an Entire Row or Column
You can select an entire row by clicking the first cell in the row and using the Shift + Spacebar shortcut. The same function for columns can be accomplished by using the Ctrl + Spacebar shortcut.
Format an Object or Chart
If you’ve inserted an object or chart into your spreadsheet, Excel makes it easy to format it. You can use the keyboard shortcut to bring up a dialogue box that contains all of the proper formatting tools you’ll need to succeed. The shortcut is Ctrl + 1.
What are some of your favorite Microsoft Excel shortcuts? Leave them in the comments.
Have You Heard of Evernote for Your Business?

Every business owner has a lot of work on their plate that can make organizing vast amounts of information difficult. Thankfully, there are software solutions out there that can be incredible assets for the business owner. Evernote is one such application. It is designed to help your business focus on completing tasks and communicating effectively. Some of the main uses that it has for business-class use is for connecting teams through a unified platform and gathering information for later review. Of course, the main purpose of Evernote is to provide a comprehensive platform for note taking and organizing notes.
Here are three of the major reasons why Evernote could prove to be a useful tool for your business’ needs.
Collect and Organize Information
Typically, you’ll have to collect a considerable amount of information about any given topic if you plan on creating a project built around it. Evernote’s purpose is to allow users to store information in one place so that it can be consumed at a glance. You can then proceed to share this information hub with anyone related to the project. Evernote allows the taking of notes, as well as clipping web pages to create a workspace filled with information needed for the task at hand. It’s even possible for Evernote to glean insights based on the information gathered.
Keep the Team Together
The way that business is done has changed considerably thanks to the Internet. Your workforce isn’t necessarily all in the same place. You might have remote workers who cannot make it to the office, as well as executives who do a lot of traveling for business purposes. Due to the nature of Evernote, you’ll keep people connected by way of its Internet app. Everyone will have access to information on any connected device, regardless of their physical location, making collaboration much easier and convenient for everyone involved.
Managing Tasks and Projects
Project management is in a category of its own in terms of frustration, especially when there are countless tasks and steps to complete throughout the duration of it. Depending on the size and scope of the project, managing all of these tasks can seem impossible. It helps to have a centralized hub that can be turned to for any assistance with organizing such an endeavor. You can keep meeting notes and other information in an easy to access hub, checklists and status updates on important deadlines, and track progress as a whole so that you always know how far along a project is in the development and implementation cycle.
If you’re struggling with project management or implementation, why not give Evernote a try? It might be just the platform you need to make sure that your projects stay organized and on-time. For any assistance with the implementation of such a solution, reach out to Catalyst Technology Group.
You Should Care About Blockchain Technology

We often go into depth about technology, management, and other business-oriented topics, and occasionally we decide to talk about a technology that may not be all that familiar to people with the hope that a short primer on the subject will ultimately help our readers to become curious and do their own research to understand the technology better. With Bitcoin being a trending topic in the news, understanding what a blockchain is will help you understand how this technology will drive data security in the coming years.
First, What Is Bitcoin?
Bitcoin is a type of digital currency. Bitcoin doesn’t exist physically, such as coinage or paper money does, but instead exists in code form. The interesting thing about Bitcoin is how it’s generated. Users can utilize high-end computing hardware (even commercially available computer hardware) to “mine” for Bitcoin and simply invent the money. Granted, there is a limited supply of Bitcoin and generating even a small amount of Bitcoin requires a lot of computer resources and a lot of time. That said, Bitcoin has become a viable currency online for many online stores. At the time of writing this, a single Bitcoin is worth about $ 17,112 USD, compared to $ 27 back in 2009.
What is Blockchain?
A blockchain is exactly as the name suggests, a series of blocks that contain information, chained together to provide a reliable and secure accounting for whatever the blockchain is set up to measure. The technique of blockchaining originated in 1991 and was developed to timestamp documents to ensure they couldn’t be tampered with or altered. It has since been tabbed “The Internet of Value” since it functions as a form of database. The differences between traditional databases and a blockchain are numerous, however.
In a blockchain, the information that is shared is both confirmed and encrypted; and, distributed over a number of linked transactions; and, automatically replicated by each user that uses the blockchain, providing users of the chain a secure and tamper-proof ledger of secure activity. This activity can be exchanges in currency, cryptocurrency, medical records, shareholder records, etc.–any information that requires a itemized and uneditable database in which to relay information.
Uses of Blockchain
Blockchain technology has been described by industry professionals as the “new Internet”, but since a majority of people have never heard of it, we thought it would be good to provide some examples of technologies that would benefit from moving on from the centralized hosted technologies that we have today to distributed hosting like blockchain. Here are a few:
- Security: The decentralization of data makes it exponentially safter to save files in multiple locations.
- Data Management: The verification data is completely transformed and more robust with blockchain.
- Logistics: Individual goods can be traced to their origin, giving companies and consumers enhanced transparency.
- Investing: Smart contracts using blockchain provide strong security for crowd-based funding and other investment.
- Internet of Things: Provides a construct to assign automation for remote systems, and the smart contracts required to give their consumers peace of mind as many IoT devices come with some privacy concerns.
Blockchain and Bitcoin
With Bitcoin being a hot-button issue in financial circles of late; and, with other cryptocurrencies popping up all the time, you can see how blockchain technology creates a construct in which a digital currency could thrive. Since there will never be more than 21 million Bitcoins in circulation, people that choose to “mine” the Internet for this cryptocurrency do so with the understanding that today it would take a hundred years or more to mine one single Bitcoin. This ceiling protects the currency from inflation. Bitcoin miners have responded, building Application Specific Integrated Circuit (ASIC) systems to specifically mine for Bitcoins, but so many people have started to mine for them (especially as their value has started to increase) that new strategies have to be implemented in order for any of these miners are to hit paydirt, so to speak. Today, many of the so-called Bitcoin miners actually mine pools of data for small pieces of BitCoin.
What a Bitcoin is worth today is what the market for Bitcoins says it’s worth–no more, no less; and, since it uses blockchain technology, you can bet that any Bitcoin that is available, is legitimate. Since users expect almost 95% of all the Bitcoins there will ever be to be released by 2024, speculators are now saying that by then a single bitcoin could be worth a staggering $ 250,000. In fact, the demand is seemingly so high that some financial institutions have started offering investors the chance to invest in Bitcoin futures, suggesting that they completely believe in the stability of the Bitcoin market; a testament to the viability and reliability of blockchain technology.
The blockchain is definitely going to be a household name soon, but for now, we hope this article can give you a small look at the technology that will help the Internet of Things be the biggest shift in technological advancement this world has ever seen. Do you have any Bitcoin, or do you know about cryptocurrency? Do you think digital money is the future of currency? Leave your thoughts with us in the comments section below.
Facebook, Gmail, and Slack are Becoming More Collaborative

In the modern business setting, collaboration drives productivity. As a result, many software developers are producing software with collaboration in mind. Since these developers are all in competition with each other for market share, they are typically trying to build on more advanced features to outmaneuver the other companies. Some of the biggest names in the industry have recently updated their products to make collaboration a priority. This week we’ll take a look at updates made to Facebook Workplace, Gmail, and Slack.
Facebook Workplace
Communication drives collaboration. Facebook has rolled out a new desktop app to work with the chat element within their productivity network app, Workplace. Called Workplace Chat, the application allows users to easily swap files and share screens for more dynamic collaborative processes. Down the road, Workplace Chat will support third-party applications to improve collaborative function for the thousands of companies that utilize the Facebook Workplace platform.
Apps for Gmail
Google’s strategy is to improve Gmail’s utility in the collaboration-minded setting of the modern business. They have begun to look to third-party developers to find collaborative solutions. Companies like RingCentral, Trello, DocuSign, Intuit and more have working integrations with Gmail, making the email provider better suited for the collaborative business than ever before. With the millions of users that utilize Gmail, and the flexibility Google is offering app developers, it’s no surprise to find out that new companies are actively creating software for the platform.
Slack Adds Improved Screen Sharing
One way to improve collaboration is with the addition of screen-sharing functionality. Slack was designed to promote collaboration in the first place, and has improved it’s screen sharing function to include interactivity. The Slack platform is intended to create employee alignment and a shared understanding of a project; and, with screen sharing capabilities updated for paid subscribers, teams that use the application will benefit from this additional functionality. Users will be able to create temporary notes, navigate through documents better, and edit documents freely, giving the whole interface a substantial upgrade.
What does your organization do to help improve collaboration? If you have a useful application that could be of help to another reader, please don’t hesitate to post it in our comments section below.

