Tip of the Week: Never Pay to Print Business Cards Again

It’s just good business to hand out your business card to prospective clients, and it has been for a very long time. As far back as the Renaissance, special guests were announced with name cards that displayed who the guest was and what types of greetings were due. It wasn’t until the Industrial Revolution that business cards became primarily a means of displaying trades or professional skills. Business cards are mostly used for marketing and networking in the modern age, and your organization should be using them.
Software developers have started to create applications that make using business cards even easier. Here are some of the features of these apps and how you can use them to your advantage.
Drop
Drop is an app that serves two major purposes. It’s basically a virtual business card, but it also lets you take a quick snapshot of any new business card you’re given and save it automatically into a contact. Now you won’t have to worry about keeping the card safe and sound in your wallet.
It’s easy to see why Drop is such a great networking tool. Since you aren’t reliant on keeping the card on your person, you will have an easier time keeping track of it in your smartphone. However, you have to watch out for the app misreading the names or looking at the wrong address.
Overall, Drop is a solid solution, and it’s compatible with both Android and iOS devices. It even has a geolocation feature that can group your cards together based on the scanning location, or extract information from a business card you had already taken a photo of. Finally, you can create your own digital business cards, which is something that you could do even without having the app installed.
CamCard
CamCard is a solution that helps your business manage its business cards, as well as scan and collect information associated with them through a mobile app. Since it’s a cloud-based service, your scanned cards can be accessed on any connected device, be it a tablet, smartphone, or your web browser. You can also annotate scanned cards for any meetings or scheduled appointments that might be associated with them.
CamCard also has a business app that you can use to share business card information with your organization’s internal sales department. You can use this app to keep your organization up-to-date on information sharing. Information can be shared to either your entire organization or by department. Furthermore, integration with Google Contacts, Outlook Contacts, and Microsoft Excel can be achieved, and you can set up user access roles based on who you want to access this vital information.
How do you manage your business cards? Let us know in the comments.
Tip of the Week: Don’t Let Your Old Android Device go to Waste

Unless you’re the trade-in or hand-me-down kind of person, it’s likely that you have a supply of old Android devices squirrelled away somewhere. You know, just in case the one who have now breaks. However, these old devices can be useful in other ways around the office. For this week’s tip, we’ll go over three alternate uses for your mobile device in the office.
Portable Trackpad
There are assorted applications available that allow you to link your old phone to your computer and use it as an alternative controller to your mouse. These apps often offer specialized features that give you better control over media playback and other useful workplace utilities.
Just be sure to install whatever app you select from the Google Play store, as it is the safest option out there for downloading apps. However, you should also make sure that your IT department signs off on you adding these apps to devices used for work.
Universal Remote
If you happen to use smart devices in your office, your old phone could become a central control hub for them. Download the necessary apps from the Google Play store, and in no time, you’ll be able to control any of the gadgets you have installed around your office with a dedicated remote, eliminating the need for the bulky included remotes that accompany many of these devices, as well as the need to take up space on your current mobile phone.
Security Camera
Similarly to using your old device as a universal remote, you can find apps on Google Play that can turn it into a security camera with a few different features. By doing so, you can boost your office’s security with the option to check in on goings-on via a web browser, record the footage, and even have the camera activate when motion is detected.
Bonus Purpose: Donate the Phone to BOINC
The Berkeley Open Infrastructure for Network Computing, or BOINC, allows you to donate the computing resources of your old phone to assist research teams in their efforts towards scientific breakthroughs. So far, resources dedicated to BOINC have powered research into the climate, molecular dynamics, genetic sequencing, measured the efficacy of malaria treatments and the power of earthquakes, as well as many other scientific causes.
To participate, all you have to do is download the BOINC app from the Google Play Store and select what research you want to commit your phone’s resources to. The app will only run if your device is both charged and plugged in, as so not to leave you with a drained phone, and can be set to only transmit data over Wi-Fi, saving your data.
What other uses have you come up with for your old Android devices? Let us know in the comments, and make sure to subscribe to our blog!
Scam Leverages Email from a Reluctant Contract Killer

To many, email scams have become a joke. Sitcoms have throwaway punchlines that reference a character getting an email from a rich uncle in Nigeria, or some friend needing funds to get home from an overseas trip. One of these scams may not at first seem to be amusing, as it threatens the recipient’s life, but if read further, proves to be quite the drama.
Upon accessing their inbox to find an email with the subject: “Please read this it can be the most important information in your life,” the target opens the message to discover that there has been an evil plot taking shape to do them in. While this email is completely a scam, it is entertaining enough to review here, if only to show how creative cybercriminals can be.
The email itself informs the recipient that the sender, a professional hitman, has been hired to execute them. According to the email, this order was passed to the contract killer because the recipient’s “activity causes trouble to a particular person.” However, after studying the target, the hitman has had a change of heart and is therefore offering the target a chance to save themselves–something that will blackball the hitman and ruin the reputation built on twelve years of successful contracts.
The recipient then learns that the hitman was looking to get out of the game anyway, and so this offers a mutually beneficial solution. For 0.5 Bitcoin (worth well over $ 5000), instead of carrying out the kill, the assassin will instead turn over the name of the person who hired them, along with incriminating evidence to bring to the police. Of course, the hitman warns, the target should not go immediately to the police, as their investigation would take longer than the two days the target has to accept the arrangement.
Finally, the hitman promises to make contact again once the funds have been transferred, and apologizes for their career, stating:
“I really regret that you became my prey.”
Despite (or perhaps due to) the letter reading like the synopsis of a summertime Hollywood blockbuster, the scammer responsible has yet to collect any funds in the online wallet they provide in their letter. Of course, this may also be in part because of the demand of the 0.5 Bitcoin, which isn’t exactly pocket change.
Now that you know this, don’t be the first to hand over a few thousand dollars for an empty threat. Instead, if you happen to receive one of these emails, mark it as spam. This will help teach the spam filters that this is an unwanted email, and might help to keep it from reaching someone else’s inbox.
For more information to help you dodge the scams that cybercriminals leverage, give Catalyst Technology Group a call at (317) 705-0333.
Looking at the Landscape of Email Fraud

Email is arguably the most popular method of business correspondence in existence. It’s fast, economical, securable, easy to store/archive, and searchable in a way that traditional, physical records can’t compete with. With billions of emails sent every day from all over the globe, there is a considerable amount of sensitive information transmitted within these communications. The criminal element is looking for every opportunity to steal and exploit personal data, as well as take advantage of vulnerabilities to gain access to a company’s data or network.
One particularly effective method of email fraud is impersonation. Sometimes falling under the categories of phishing, whaling, or SMiShing, impersonation email emulates a legitimate address from a non-threatening source that convinces the user to take an action. An example of an impersonating email fraud would be a user transferring funds to a 3rd party account on the order of what they believe is a legitimate message from their CEO, but actually originates from a spoofed email address. Another example would be if someone opened an email attachment that appeared to be a legitimate spreadsheet but actually introduces ransomware into their network.
Email Security by the Numbers
For those who are looking to visualize the risks associated with email fraud, here’s a look at a few recent statistics that show just how big of a problem it can be for a business.
- In 2017, the number of worldwide email users will top 3.7 billion, or about half of the worldwide population uses email in 2017.
- Phishing attacks make up about 91% of all attempted cyberattacks.
- Top three reasons people are duped by phishing emails are curiosity (13.7%), fear (13.4%), and urgency (13.2%).
- Email fraud was the 2nd most frequent successful external intrusion method in 2017.
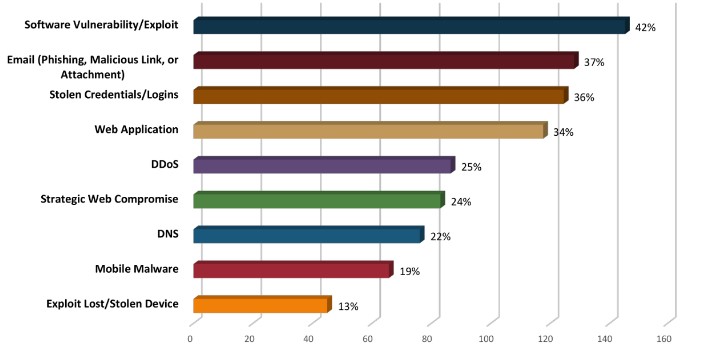
- 0.5% of the top million domains are protected from impersonation by email authentication.
- Implementing email authentication would save the average company $ 8.1 million per year in cybercrime costs—$ 16.2 billion annually across the Fortune 2000.
- Business Email Compromise (BEC), also known as CEO impersonation, losses are up 1,300%
Reducing your Business’ Risk of Email Fraud
Most email security experts agree that implementing two encryption and authentication standards are the first steps to reducing the number of cyber security gaps that have been proven to increase risk of email fraud.
- DMARC: The first standard, Domain-based Message Authentication, Reporting, and Conformance, or DMARC, authenticates an email domain, ensuring that the sender’s information aligns with the known information about the authenticated domain. DMARC has been found to detect the majority of email spoofing and impersonation and handle them according to the receiver’s procedure – usually by flagging them as spam.
- STARTTLS: The second standard, called STARTTLS, is a command that orders a secured connection that subsequently encrypts the email data being sent and received.
DMARC and STARTTLS standards have proved so effective at email fraud prevention that, on October 16, 2017, the U.S. Department of Homeland Security ordered ALL federal agencies to implement both of them within 90 days.
Federally Mandated Email Regulations for Businesses
DHS isn’t the only organization requiring email encryption as part of their technology regulations and compliances.
- HIPAA: Those entities in the healthcare industry that are required to be in compliance with the Health Insurance Portability and Accountability Act (HIPAA) must implement access controls, audit controls, integrity controls, ID authentication, and transmission security before an email correspondence that includes personal health information is considered to be “in compliance”.
- PCI-DSS: Companies that use customer credit card information are required to meet PCI data security standard. The PCI-DSS expressly advises organizations to never use email, encrypted or otherwise, to share credit card data. Because emails are generally stored for long periods of time, it violates the PCI rules regarding card information storage after authorization and maintenance of access control at all times. Still, many PCI compliant businesses choose to use email encryption as an additional security measure.
Catalyst Technology Group Has Your Back!
For most small businesses, the idea of tackling any type of email fraud prevention on their own is extremely overwhelming. It’s a world of protocols and acronyms that the average IT decision maker often prefers to avoid altogether – and that’s just encryption. To get the maximum productivity while maintaining network and data security, modern businesses should leverage spam filters, antivirus and malware scanning, archiving/storage, hosting considerations, acceptable use policies, access control, and more. In the end, an email solution can have a large impact on a company’s daily operations.
The good news is that you don’t have to fight cybercriminals alone! Catalyst Technology Group is well acquainted with all types of cybersecurity – including email authentication and encryption. Our experts will help you find the perfect email fraud protection strategy to meet the needs of your business. Contact us at (317) 705-0333 and get encrypted.
Social Media is Spurring Business Growth

Social media has an interesting place in the business world, sitting somewhere between incredibly helpful and downright dangerous for your organization. It’s important that you consider how your business is affected by social media so that you can both leverage it to your advantage and minimize the risks associated with it.
Many of the popular social media platforms are being used in the world of business, including Facebook, Twitter, LinkedIn, YouTube, and even other apps like Snapchat and Instagram–all of which have their own distinct uses. However, they all have considerable benefits and risks that extend beyond the individual platforms. Here are some of the benefits that social media can pose for your organization.
The Benefits
The primary benefit associated with social media is right in the name–it’s social. You provide your business with exposure across the Internet, meaning that your organization is being seen by prospective clients. On the other hand, you’re also being seen by competitors, who might choose to use the information that they see as a blueprint toward one-upping your organization’s outreach efforts. Either way, the point stands that you’re connecting with potential buyers or customers, which is a valuable way to make your organization known.
The Risks
Despite the benefits, there are many risks associated with social media networks. Among the most important are security and productivity, both of which could derail operations as you know them.
- Security: When you sign your organization up for a social media network, you’re providing another outlet for a hacking attack. If your business has a website, you’re aware of the online threats that could pose a threat for your business. Many of the same threats, including password and username theft, can become a problem for organizations that aren’t careful. Even spam can be an issue, as you might be dealing with suspicious messages from “interested buyers.” The best way to stay safe while using social media for business purposes is to understand best practices. Don’t accept connections to suspicious individuals or organizations, and ensure that any passwords or usernames are as complex as can be.
- Productivity: In regards to employee productivity, your organization could face down a considerable loss of work quality or quantity as a result of personal social media use during work hours. What this means is that your employees might be too busy browsing cat videos or sharing memes with each other to focus on their work. Of course, this doesn’t necessarily apply to all of your hard-working employees, but all it takes is a few to ruin a good thing for everyone. Therefore, you need to take measures to keep employees from wasting time on social media when they are supposed to be working.
A content filtering solution as part of a Unified Threat Management (UTM) solution can keep employees from wasting time on social media or potentially dangerous websites on a per-user basis. This can keep problem employees from visiting these sites while also maintaining access for your marketing team and employees who can manage the access properly. To learn more, reach out to Catalyst Technology Group at (317) 705-0333.
Fiber Optics Are Boosting the Speed of Business

The dissemination of data is of vital importance for your business, but do you understand why? Depending on the way your infrastructure is set up, you might be holding your organization back through the use of antiquated technologies. In a lot of ways, advances in technology have allowed businesses to achieve faster connection speeds–particularly in regards to connecting to the Internet.
The dissemination of data is of vital importance for your business, but do you understand why? Depending on the way your infrastructure is set up, you might be holding your organization back through the use of antiquated technologies. In a lot of ways, advances in technology have allowed businesses to achieve faster connection speeds–particularly in regards to connecting to the Internet.
Compared to old-fashioned cables, fiber-optic cables and connections could prove to be a spectacular way to transmit and receive information in the coming years. But what’s the major difference?
What is a Fiber Optic Cable?
What might seem like an ordinary network cable is truly something extraordinary. A fiber optic cable is constructed using glass fibers inside an insulated casing. They basically transfer data through the use of light pulses. Light travels through the core of the cable, which is insulated by countless glass strands that allow the light to travel through bends in them. There are two different kinds of fiber optic cables. Single-mode fibers use glass strands to generate light, while multi-mode fiber optic cables use LEDs to generate light. This light is responsible for the transfer of data.
How Fast is It?
Your business might be used to broadband Internet connections, but we’re going to use fiber optic cables for our example. Generally speaking, a broadband connection is going to be much slower than fiber optic cable networks. You might remember the painful experience that dial-up Internet provided many years ago, as well as how great of an upgrade broadband Internet was at the time. In much the same way, fiber optic cabling provides speeds that far exceed the expectations set by broadband.
For example, if you want to download a 45-minute television episode, the standard 20mbps speed offered by a broadband connection will finish the task in about 1.5 minutes. The same task could be accomplished by a fiber optic connection in around 1.7 seconds–a considerable improvement to say the least.
The Benefits
In addition to the much faster speeds offered by fiber optic cables, they also provide your organization with many other benefits, including the following:
- Higher capacity: Fiber optic cables provide more bandwidth for your organization’s connection.
- Higher signal strength: You can forget about signal boosters–light travels at a greater speed and distance without losing its strength.
- More consistent: Light-speed data is less susceptible to interference from electrical appliances, like the break room microwave.
Does your business need help with implementing a faster and more efficient network? Fiber optic cables are also an option for your organization’s in-house network. To learn more, reach out to us at (317) 705-0333.
Take Advantage of Comprehensive Network Security with UTM

Network security is one thing that rarely stays the same for any business–especially with the ever-changing threat landscape on the Internet. No matter how much time you spend preparing for security troubles, you’ll always be caught unawares if you never assume that the worst will happen. You should be taking advantage of both traditional security solutions, as well as new and emerging tools that help you keep advanced threats at bay.
Regardless of how much your business’ technology grows, there is always going to be the possibility that even some basic threats could cause trouble for your organization. For example, your workstation will be vulnerable to threats like viruses, malware, spam, and many others if you choose to forego traditional protection solutions like an antivirus or firewall. Furthermore, even consumer-grade protections are often not enough to keep more advanced threats at bay.
It’s all a matter of cost. Managed service providers make these services more affordable for small businesses. A Unified Threat Management (UTM) tool is the ideal solution for many SMB security woes. A UTM includes enterprise-class solutions like a firewall and antivirus that keep threats from making an impact against your business, as well as spam protection and content filtering to keep issues out of your infrastructure in the first place. This saves you a considerable amount of time and money, as eliminating threats after the fact can be both wasteful and risky.
There are also other security solutions that you’ll want to consider, namely two-factor authentication and biometrics. Two-factor authentication allows your organization to add a secondary credential to any login portal so that hackers have more trouble accessing sensitive information. An example of a two-factor authentication system is having a code sent to your smart device, which would then be input following your password. Hackers don’t want to do more work than necessary, so if you make accessing your account challenging, they are less likely to pursue the opportunity.
Biometrics make things more complicated for hackers as well. Biometric technology uses your body’s natural identification systems to ensure that only you are accessing your accounts. Scanning your iris or fingerprints are two examples of biometrics that keep hackers from cracking your security protocol. Unless a hacker has a picture-perfect copy of your eyes or fingers, they’ll have a difficult time stealing anything from your accounts.
How does your business keep itself safe from hacking attacks? Regardless, Catalyst Technology Group can help. To learn more, reach out to us at (317) 705-0333.
Proper Hard Drive Disposal is An Involved Process
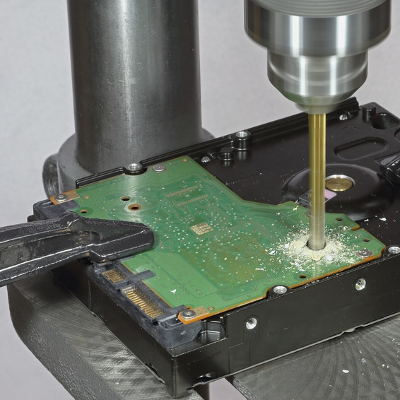
When a business utilizes any kind of technology, there will come a time when that technology needs to be replaced–which means that the business will need to be sure that any data on the old machines cannot be recovered. This, in turn, means that the machine’s hard drive must be destroyed. In order to be absolutely certain that this has been accomplished, it helps to lean on the guidelines established by HIPAA.
Why HIPAA is Important
HIPAA, or the Health Insurance Portability and Accountability Act of 1996, was intended to do two things: first, protect the health insurance coverage of workers as they change their employment, and secondly (and more relevant to this topic) to protect the availability and privacy of health data. Part of preserving the privacy of this health data is ensuring that there aren’t extra copies of it lying around, waiting to be recovered.
This is a particularly crucial point, as medical professionals maintain a considerable amount of their patients’ data on their systems. Should they simply throw out an old computer without dealing with the hard drive (or upgrade to a new drive without doing the same) they open themselves up to serious consequences and liabilities. For this reason, HIPAA includes requirements that these providers must follow to prevent this from happening.
Destroying Data
Somewhat surprisingly, HIPAA doesn’t specifically outline any procedures for acceptable data destruction, although it does offer suggested methods. These range from magnetizing (or degaussing) the drive-in question to eliminate the data, to simply smashing it. Other common methods of destroying a disk drive involve running a drill through it.
However, to truly ensure your data security, you’ll want to take it a few steps further.
In order to really ensure your compliance to the standards outlined in HIPAA, it is best to lean on the resources of a professional. Rather than relying on blunt force trauma to destroy an unwanted drive, a pro can literally shred the drive with specialized equipment.
Catalyst Technology Group can handle the disposal of your equipment on your behalf, allowing you to focus on putting your new solutions to work for your benefit. For more information, reach out to us at (317) 705-0333.
Tip of the Week: Why You Should Reconsider Your Best Practices

The term “best practice” has been used by businesses for years to describe the optimal way of performing a particular task. However, before fully adopting them into business operations, it is important for these practices to be examined and deemed to be beneficial to an individual company’s circumstances. If they are not, a company risks much by adopting a misplaced best practice.
The major problem is that “best practices,” while useful if applied properly, is a term that has largely become a buzzword for businesses to use in their communications. This is dangerous, as there is a lot put at stake based on the term “best practice” alone. Therefore, it is crucial that so-called best practices are reviewed and examined before a business puts strategies based on these practices into place.
This was the argument made by Professor Freek Vermeulen in his recent book, Breaking Bad Habits: Defy Industry Norms and Reinvigorate Your Business. An interview with the Harvard Business Review allowed him to discuss the phenomenon further.
To provide an example of how best practices may not always be of a business’ best interest to follow, Vermeulen discussed a South African bank called Capitec and how they relied on reverse benchmarking to identify how to become an outlier in their industry.
The practice of reverse benchmarking can be summed up as the process of examining how one’s industry typically operates in order to identity weak spots in accepted practices and improve internal business operations. This can often lead to the abandonment of what is considered the status quo, if not heavily modifying it.
Capitec’s examinations revealed that other banks in South Africa had a tendency to close at four o’clock in the afternoon. To abandon this status quo, industry-standard practice, Capitec not only extended their hours to enable those who worked during the day to see to their banking needs once their work day was over, they even implemented Saturday hours in many of their branches. As a result, Capitec has since carved out a healthy market share for themselves.
This account is just one example that shows how what is standard practice might not be what is best for the business following it. However, many businesses give some push back when directly asked why they follow the practices they follow. These businesses often will respond with some statement that essentially says “this is what is comfortable” or “this is how it has always been done.” These answers are a good sign that, according to Vermeulen, an organization needs to run a self-audit to determine if they are enacting practices because they benefit the organization, or if they are simply resisting change.
Furthermore, there is the risk inherent in assuming that something that made a business successful is automatically a best practice. As Vermeulen mentioned in his interview, many companies who have reached the top may have simply been lucky as they enacted risk-laden strategies, and most of the companies who tried similar strategies have long since failed and been forgotten.
Of course, changing established practices and patterns is not easy for businesses to do. Vermeulen notes this, stating that many companies will hold out until they have no choice but to make a change. This is usually done at the point where their profits and productivity take a hit. However, waiting until this point often makes change more difficult for these companies. According to Vermeulen, the key to avoiding unnecessary difficulty is simple: “Be proactive.”
By taking the opportunity to audit your business practices before your company is stuck in a life or death situation, you can more clearly see where your company is weakest. Better yet, you will be able to remedy these weaknesses before your company is at risk.
Catalyst Technology Group can help you evaluate your IT solutions to ensure that they are not contributing to any weaknesses that your company may suffer from. Call us at (317) 705-0333 for more information.
Which is More Secure, Your Mobile Network or Wi-Fi?

For the modern business, having a strategy to manage your employees smartphone use is essential. This is because most of the people that work for you have smartphones. One study shows that upwards of 90 percent of people under 30 own a smartphone. If you have any design on running a business, or employing millennials (who are the largest generation in the current workforce), you’ll need to know what you are doing to protect your business from the increasing amount of threats that are out there targeting smartphones.
An annual Wi-Fi Security Report conducted by Wandera found that, out of a sample of 100,000 corporate-owned mobile devices, 74% of wireless data was transferred using a Wi-Fi network, 12 percent of Wi-Fi hotspots used by those people are open and lacking encryption, and only four percent of these corporate-owned devices have been exposed to malware through an accidental or deliberate man-in-the-middle attack.
The man-in-the-middle attack (MiTM) is one where a computer will pick up malware that allows an intermediary to intercept files and correspondence between the two machines, and upon connecting to a network via a Wi-Fi connection, transfers the malware onto the computing network–thus infecting the network with the malware that allows the hacker to intercept any communication.
It’s largely understood that cellular networks are more secure than Wi-Fi networks, as cellular networks utilize high-end encryption techniques. This doesn’t make them popular, however. People will typically use Wi-Fi that is available. In fact, one statistic suggests that people are so addicted to the use of Wi-Fi that upwards of 60 percent of people will connect to any available public Wi-Fi rather than use the cellular data, even if they don’t pay for it themselves. Symantec’s Wi-Fi Risk Report corroborates this notion, adding that roughly the same number of people believe their personal information is more secure transmitted over Wi-Fi, and that 53 percent cannot tell the difference between a secure and unsecure Wi-Fi network. The report goes on to state that nearly nine out of ten consumers have put their information at risk by using public Wi-Fi.
At the business level things get a little better. While individual Wi-Fi use remains similar, businesses typically do a much better job of securing their network to keep malicious entities out. One way they do this is by setting up a firewall to keep their Wi-Fi networks away from the rest of their network. Typically, when a person accesses your organization’s Wi-Fi, they are then able to access your whole entire network. If your servers and other confidential data are linked to your organizational Wi-Fi, then an intruder who can manage to connect will then have access. By separating your Wi-Fi from your network behind a firewall, you will not only protect yourself from ambitiously malignant people on your network, but also go a long way toward safeguarding your network from cyber attacks in general.
Another way that the business can ensure their mobile strategy won’t hamstring their company’s network is by instituting a Virtual Private Network (VPN). The VPN brings additional encryption to data communication by creating a secure tunnel in which to transfer data. For the small business a VPN has become an almost essential part of providing your staff with a workable remote computing situation. Not only does it work to secure your business’ data while using available remote connections, it makes it easier to scale a business by allowing new systems to connect to it with minimal configuration. In doing so, the deployment of a strategic VPN reduces capital investment and is a major benefit for organizational mobility.
If you haven’t already, your business is going to have to address your mobile security before it gets burned. If you would like to learn more about what you are up against, or how you can utilize today’s security technology to protect your business’ important data, call Catalyst Technology Group today at (317) 705-0333.

